SY0-601 Exam Dumps - CompTIA Security+ Exam 2023
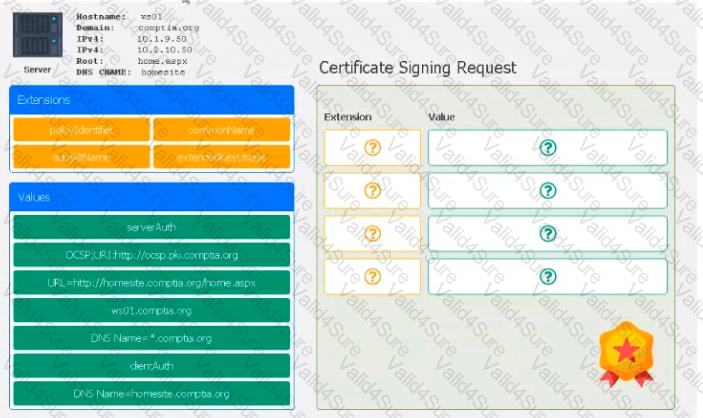
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
• Hostname: ws01
• Domain: comptia.org
• IPv4: 10.1.9.50
• IPV4: 10.2.10.50
• Root: home.aspx
• DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.
A security team is providing input on the design of a secondary data center that has the following requirements:+ Anatural disaster at the primary site should not affect the secondary site. The secondary site should have the capability for failover during traffic surge situations.+ The secondary site must meet the same physical security requirements as the primary site. The secondary site must provide protection against power surges and outages.
Which of the following should the security team recommend? (Select two).
A security administrator Is evaluating remote access solutions for employees who are geographically dispersed. Which of the following would provide the MOST secure remote access? (Select TWO).
An employee used a corporate mobile device during a vacation Multiple contacts were modified in the device vacation Which of the following method did attacker to insert the contacts without having 'Physical access to device?
A company is focused on reducing risks from removable media threats. Due to certain primary applications, removable media cannot be entirely prohibited at this time. Which of the following best describes the company's approach?
Security engineers are working on digital certificate management with the top priority of making administration easier. Which of the following certificates is the best option?
A company needs to enhance Its ability to maintain a scalable cloud Infrastructure. The Infrastructure needs to handle the unpredictable loads on the company's web application. Which of the following
cloud concepts would BEST these requirements?
Which of the following social engineering attacks best describes an email that is primarily intended to mislead recipients into forwarding the email to others?
 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated