SY0-601 Exam Dumps - CompTIA Security+ Exam 2023
A company has numerous employees who store PHI data locally on devices. The Chief Information Officer wants to implement a solution to reduce external exposure of PHI but not affect the business.
The first step the IT team should perform is to deploy a DLP solution:
A security administrator examines the ARP table of an access switch and sees the following output:
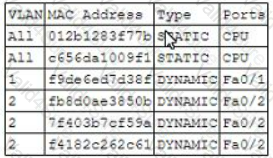
Which of the following is a potential threat that is occurring on this access switch?
A software developer used open-source libraries to streamline development. Which of the following is the greatest risk when using this approach?
Which of the following procedures would be performed after the root cause of a security incident has been identified to help avoid future incidents from occurring?
A company completed a vulnerability scan. The scan found malware on several systems that were running older versions of Windows. Which of the following is MOST likely the cause of the malware infection?
Which of the following would provide guidelines on how to label new network devices as part of the initial configuration?
Which of the following describes business units that purchase and implement scripting software without approval from an organization's technology Support staff?
An organization needs to implement more stringent controls over administrator/root credentials and service accounts. Requirements for the project include:
* Check-in/checkout of credentials
* The ability to use but not know the password
* Automated password changes
* Logging of access to credentials
Which of the following solutions would meet the requirements?