SY0-601 Exam Dumps - CompTIA Security+ Exam 2023
A Chief information Officer is concerned about employees using company-issued laptops to steal data when accessing network shares Which of the following should the company implement?
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a risk of this practice?
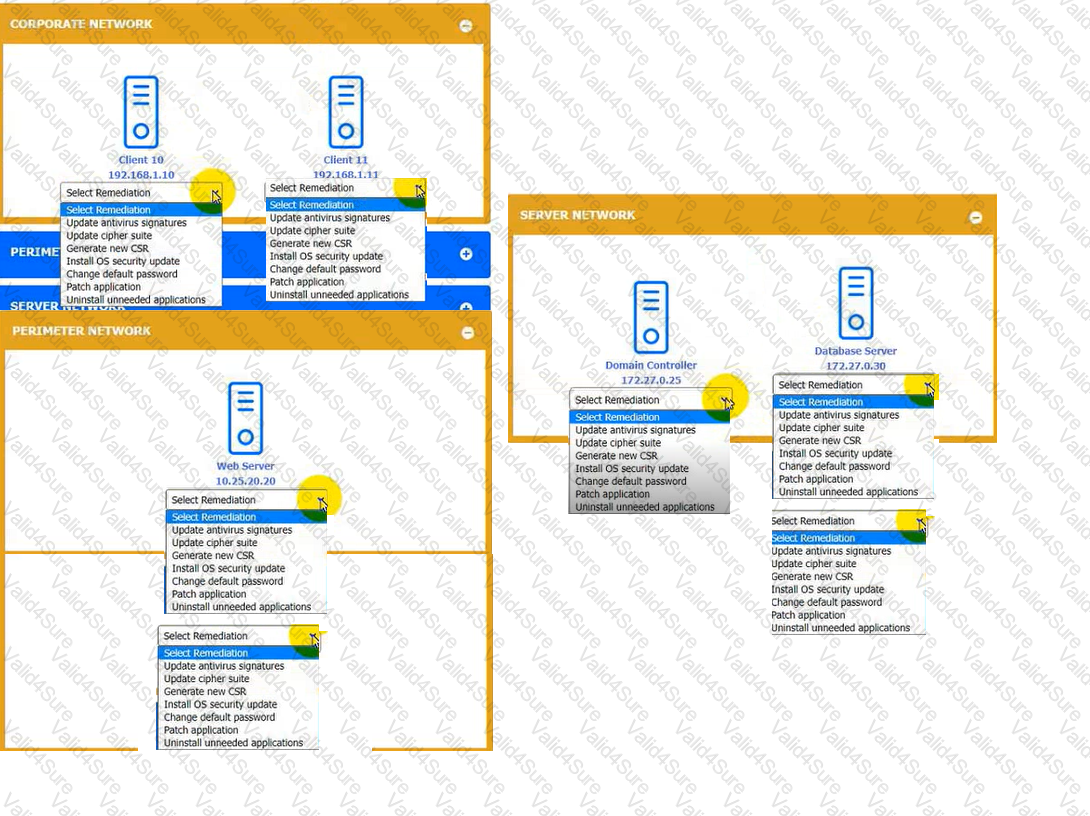
You received the output of a recent vulnerability assessment.
Review the assessment and scan output and determine the appropriate remedialion(s} 'or «ach dewce.
Remediation options may be selected multiple times, and some devices may require more than one remediation.
If at any time you would like to biing bade the initial state ot the simulation, please dick me Reset All button.
A security analyst was deploying a new website and found a connection attempting to authenticate on the site's portal. While Investigating The incident, the analyst identified the following Input in the username field:
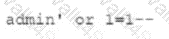
Which of the following BEST explains this type of attack?
A security researcher is using an adversary's infrastructure and TTPs and creating a named group to track those targeted Which of the following is the researcher MOST likely using?
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
A company acquired several other small companies The company thai acquired the others is transitioning network services to the cloud The company wants to make sure that performance and security remain intact Which of the following BEST meets both requirements?
Which of the following disaster recovery tests is the LEAST time consuming for the disaster recovery team?
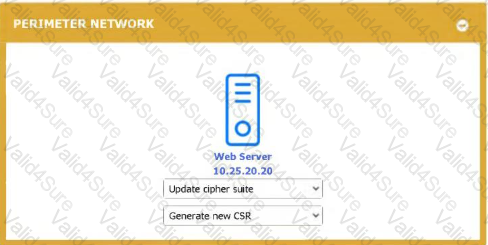
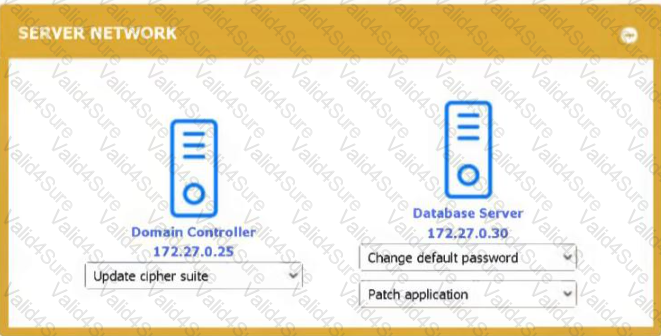 Graphical user interface, application, website, Teams
Description automatically generated
Graphical user interface, application, website, Teams
Description automatically generated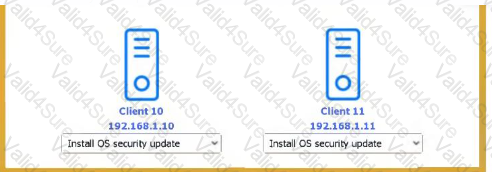 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated