Vault-Associate Exam Dumps - HashiCorp Certified: Vault Associate (002)
Searching for workable clues to ace the HashiCorp Vault-Associate Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s Vault-Associate PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which statement describes the results of this command: $ vault secrets enable transit
Which of the following is a machine-oriented Vault authentication backend?
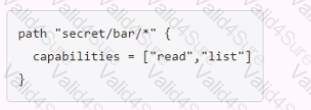
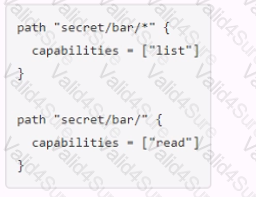
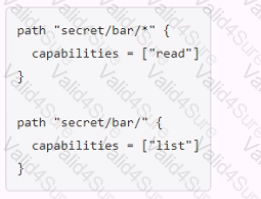
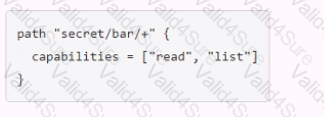
You have been tasked with writing a policy that will allow read permissions for all secrets at path secret/bar. The users that are assigned this policy should also be able to list the secrets. What should this policy look like?
A developer mistakenly committed code that contained AWS S3 credentials into a public repository. You have been tasked with revoking the AWS S3 credential that was in the code. This credential was created using Vault's AWS secrets engine and the developer received the following output when requesting a credential from Vault.
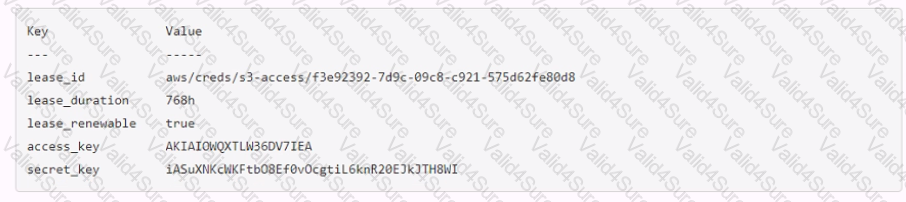
Which Vault command will revoke the lease and remove the credential from AWS?
A web application uses Vault's transit secrets engine to encrypt data in-transit. If an attacker intercepts the data in transit which of the following statements are true? Choose two correct answers.
Use this screenshot to answer the question below:
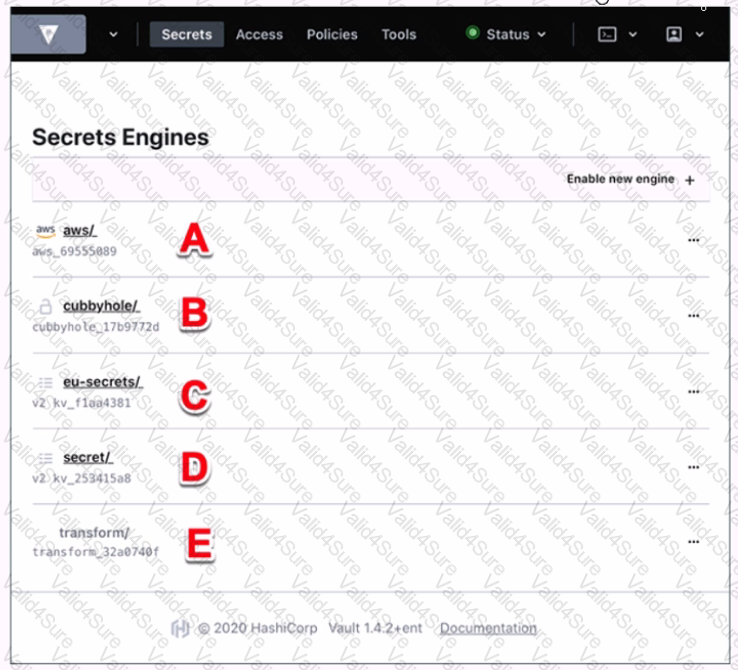
Where on this page would you click to view a secret located at secret/my-secret?
Which of the following cannot define the maximum time-to-live (TTL) for a token?