XK0-005 Exam Dumps - CompTIA Linux+ Exam
Searching for workable clues to ace the CompTIA XK0-005 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s XK0-005 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following files holds the system configuration for journal when running systemd?
A user is asking the systems administrator for assistance with writing a script to verify whether a file exists. Given the following:
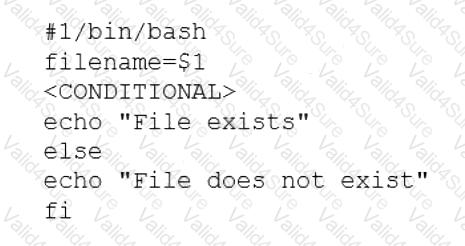
Which of the following commands should replace the
An administrator logs in to a Linux server and notices the clock is 37 minutes fast. Which of the following commands will fix the issue?
Users are unable to create new files on the company's FTP server, and an administrator is troubleshooting the issue. The administrator runs the following commands:
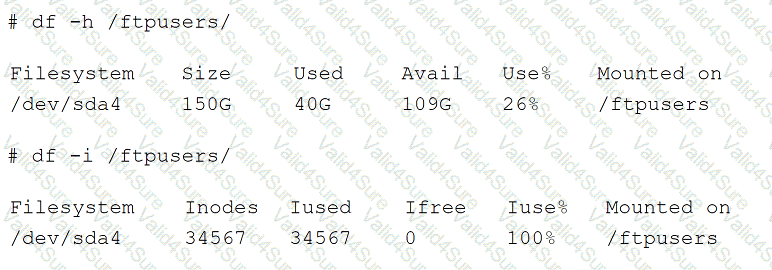
Which of the following is the cause of the issue based on the output above?
A Linux administrator wants a permission bit on a shared folder that allows only the owner of the file within that directory or the root user to delete or rename the file. Which of the following commands will help achieve this goal?
A Linux administrator is troubleshooting an issue in which an application service failed to start on a Linux server. The administrator runs a few commands and gets the following outputs:
Based on the above outputs, which of the following is the MOST likely action the administrator should take to resolve this issue?
A junior administrator is trying to set up a passwordless SSH connection to one of the servers. The administrator follows the instructions and puts the key in the authorized_key file at the server, but the administrator is still asked to provide a password during the connection.
Given the following output:
Which of the following commands would resolve the issue and allow an SSH connection to be established without a password?