200-201 Exam Dumps - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Question # 51
Which step in the incident response process researches an attacking host through logs in a SIEM?
Question # 52
Refer to the exhibit.
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
Question # 53
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Question # 54
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Question # 56
Refer to the exhibit.
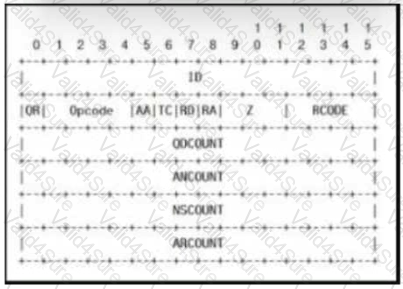
Which field contains DNS header information if the payload is a query or a response?