200-201 Exam Dumps - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
An engineer must configure network systems to detect command-and-control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology must be used to accomplish this task?
Which action matches the weaponization step of the Cyber Kill Chain Model?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump†tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
What is the difference between the rule-based detection when compared to behavioral detection?
Refer to the exhibit.
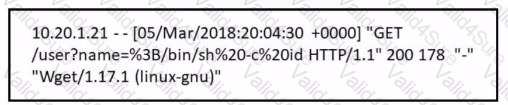
Which attack is being attempted against a web application?
Drag and drop the event term from the left onto the description on the right.