200-201 Exam Dumps - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
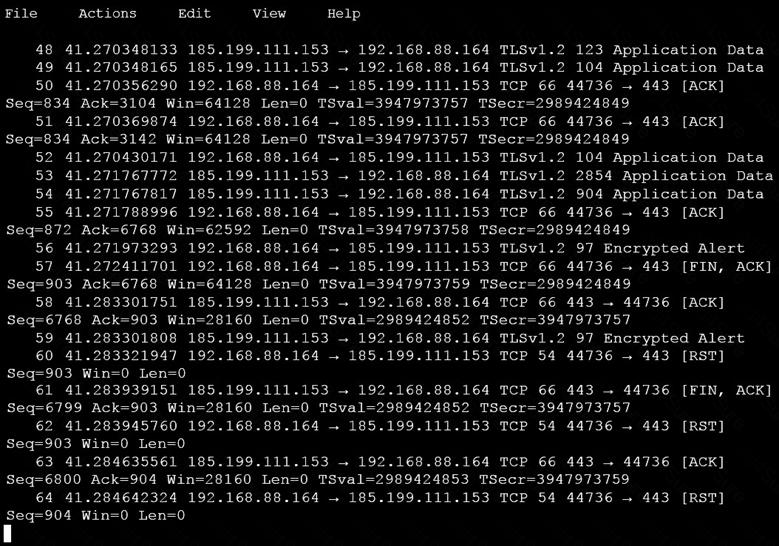
Which obfuscation technique is the attacker using?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
What is the impact of false positive alerts on business compared to true positive?
Refer to the exhibit.
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?