200-201 Exam Dumps - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Question # 65
Refer to the exhibit.
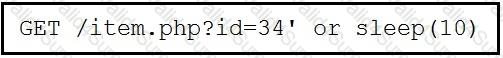
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Question # 66
Drag and drop the uses on the left onto the type of security system on the right.
Question # 67
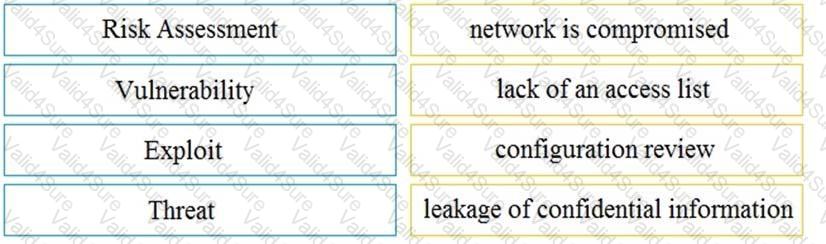
Drag and drop the security concept on the left onto the example of that concept on the right.
Question # 68
Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Question # 70
What are the two characteristics of the full packet captures? (Choose two.)