200-301 Exam Dumps - Cisco Certified Network Associate
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
Refer to the exhibit.
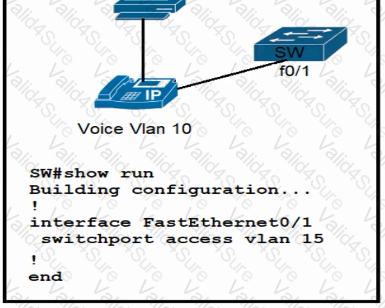
All VLANs are present in the VLAN database. Which command sequence must be applied to complete the configuration?
What is the advantage of separating the control plane from the data plane within an SDN network?
Refer to the exhibit.
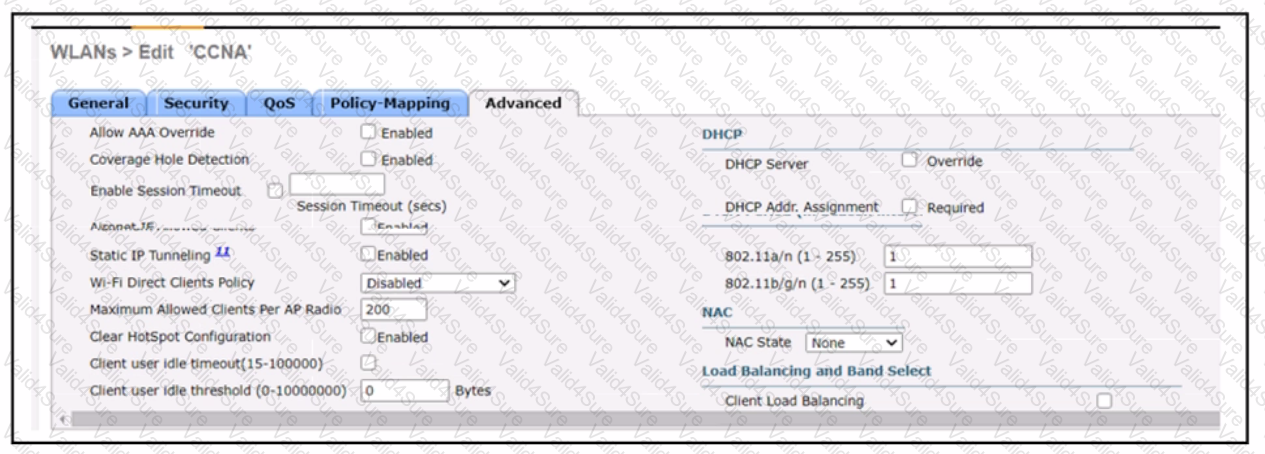
A network engineer configures the CCNA WLAN so that clients must authenticate hourly and to limit the number of simultaneous connections to the WLAN to Which two actions complete this configuration? (Choose two.)
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the next-hop devices are different?
Refer to the exhibit.
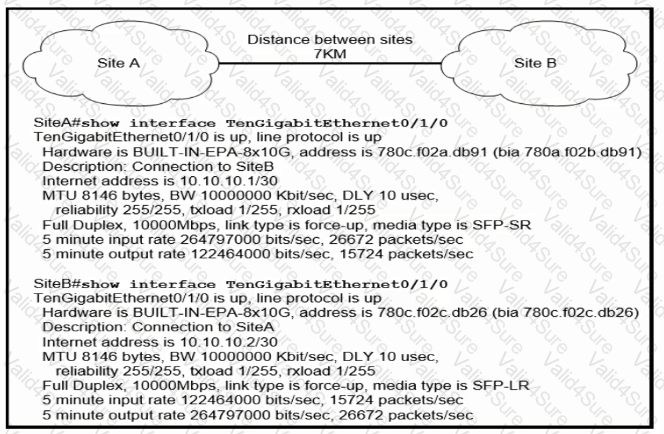
Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?
Which type of network attack overwhelms the target server by sending multiple packets to a port until the half-open TCP resources of the target are exhausted?