200-301 Exam Dumps - Cisco Certified Network Associate
Why is UDP more suitable than TCP tor applications that require low latency, such as VoIP?
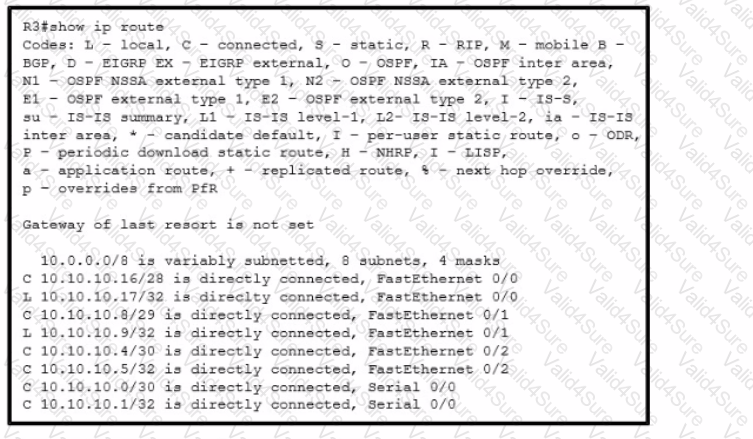
Refer to the exhibit. Which interface does a packet take to reach the destination address of 10.10.10.147?
How does machine learning improve the detection of unauthorized network access?
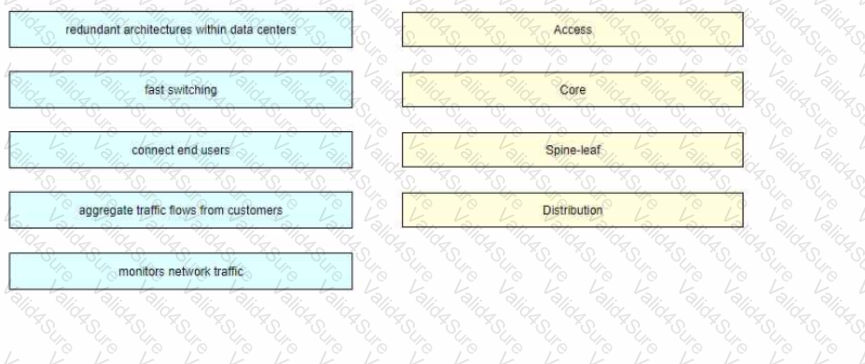
Drag and drop the common functions from the left onto the cofresponding network topology architecture layer on the right. Not all common functions are used.
A corporate office uses four floors in a building
• Floor 1 has 24 users
• Floor 2 has 29 users
• Floor 3 has 28 users
•Floor 4 has 22 users
Which subnet summarizes and gives the most efficient distribution of IP addresses for the router configuration?
Which action does the router take as rt forwards a packet through the network?