200-301 Exam Dumps - Cisco Certified Network Associate
Which WLC management connection type is vulnerable to man-in-the-middIe attacks?
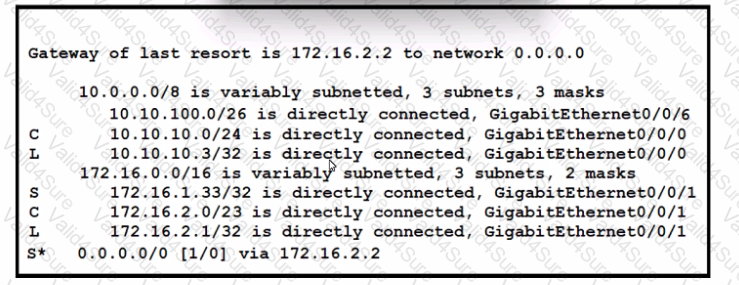
Refer to the exhibit. A packet sourced from 10.10.10.32 is destined for the Internet. What is the administrative distance for the destination route?
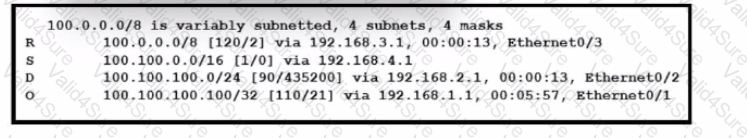
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
What is the main difference between traditional networks and controller-based networking?
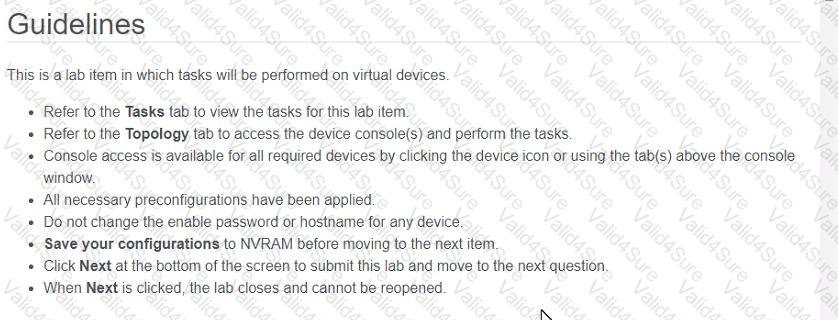
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
Which authentication method requires the user to provide a physical attribute to authenticate successfully?

Refer to the exhibit. A network engineer updates the existing configuration on interface fastethernet1/1 switch SW1. It must establish an EtherChannel by using the same group designation with another vendor switch. Which configuration must be performed to complete the process?