220-1102 Exam Dumps - CompTIA A+ Certification Core 2 Exam
A technician needs to exclude an application folder from being cataloged by a Windows 10 search. Which of the following utilities should be used?
A technician is installing new software on a macOS computer. Which of the following file types will the technician MOST likely use?
An Android user contacts the help desk because a company smartphone failed to complete a tethered OS update A technician determines there are no error messages on the device Which of the following should the technician do NEXT?
A technician is investigating an employee's smartphone that has the following symptoms
• The device is hot even when it is not in use.
•Applications crash, especially when others are launched.
• Certain applications, such as GPS, are in portrait mode when they should be in landscape mode.
Which of the following can the technician do to MOST likely resolve these issues with minimal impact? (Select TWO).
A department has the following technical requirements for a new application:
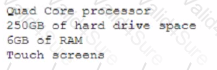
The company plans to upgrade from a 32-bit Windows OS to a 64-bit OS. Which of the following will the company be able to fully take advantage of after the upgrade?
Once weekly a user needs Linux to run a specific open-source application that is not available for the currently installed Windows platform. The user has limited bandwidth throughout the day. Which of the following solutions would be the MOST efficient, allowing for parallel execution of the Linux application and Windows applications?
A user's smartphone data usage is well above average. The user suspects an installed application is transmitting data in the background. The user would like to be alerted when an application attempts to communicate with the internet. Which of the following BEST addresses the user's concern?
A user is unable to use any internet-related functions on a smartphone when it is not connected to Wi-Fi When the smartphone is connected to Wi-Fi the user can browse the internet and send and receive email. The user is also able to send and receive text messages and phone calls when the smartphone is not connected to Wi-Fi. Which of the following is the MOST likely reason the user is unable to use the internet on the smartphone when it is not connected to Wi-Fi?