220-1102 Exam Dumps - CompTIA A+ Certification Core 2 Exam
A user clicked a link in an email, and now the cursor is moving around on its own. A technician notices that File Explorer is open and data is being copied from the local drive to an unknown cloud storage location. Which of the following should the technician do first?
A user’s Windows 10 workstation with an HDD is running really slowly. The user has opened, closed, and saved many large files over the past week. Which of the following tools should a technician use to remediate the issue?
A company recently outsourced its night-shift cleaning service. A technician is concerned about having unsupervised contractors in the building. Which of the following security measures can be used to prevent the computers from being accessed? (Select two).
A SOHO client is having trouble navigating to a corporate website. Which of the following should a technician do to allow access?
A large company is selecting a new Windows operating system and needs to ensure it has built-in encryption and endpoint protection. Which of the following Windows versions will MOST likely be selected?
Which of the following macOS features can help a user close an application that has stopped responding?
After clicking on a link in an email a Chief Financial Officer (CFO) received the following error:
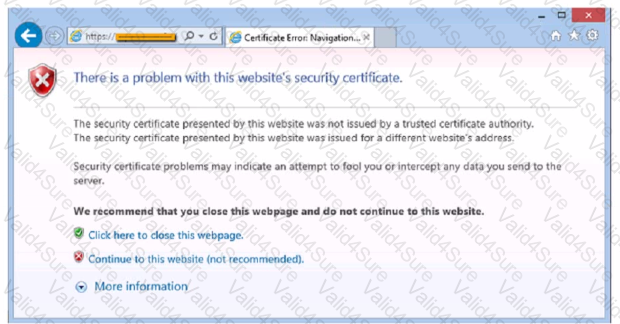
The CFO then reported the incident to a technician. The link is purportedly to the organization's bank. Which of the following should the technician perform FIRST?
While browsing the internet, a customer sees a window stating antivirus protection is no longer functioning Which of the following steps should a technician take next? (Select two).