CAS-003 Exam Dumps - CompTIA Advanced Security Practitioner (CASP) Exam
An enterprise solution requires a central monitoring platform to address the growing networks of various departments and agencies that connect to the network. The current vendor products are not adequate due to the growing number of heterogeneous devices. Which of the following is the primary concern?
A new database application was added to a company’s hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company’s cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security do to help mitigate future attacks within the VM environment? (Choose two.)
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.
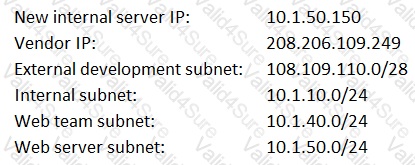
Below is a snippet from the firewall related to that server (access is provided in a top-down model):
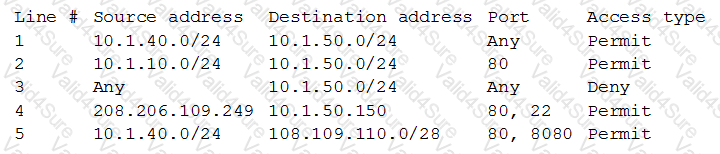
Which of the following lines should be configured to allow the proper access? (Choose two.)
An analyst is investigating behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the “compose†window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
Following the merger of two large companies the newly combined security team is overwhelmed by the volume of logs flowing from the IT systems The company's data retention schedule complicates the issue by requiring detailed logs to be collected and available for months. Which of the following designs BEST meets the company's security and retention requirement?
An organization is creating requirements for new laptops that will be issued to staff One of the company's key security objectives is to ensure the laptops nave hardware-enforced data-at-rest protection tied to permanent hardware identities. The laptops must also provide attestation for secure boot processes To meet these demands, which of the following BEST represent the features that should be included in the requirements set? (Select TWO.)
A security is assisting the marketing department with ensuring the security of the organization’s social media platforms. The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls The following configurations already are in place
• Keyword Mocking based on word lists
• URL rewriting and protection
• Stopping executable files from messages
Which of the following is the BEST configuration change for the administrator to make?