CAS-003 Exam Dumps - CompTIA Advanced Security Practitioner (CASP) Exam
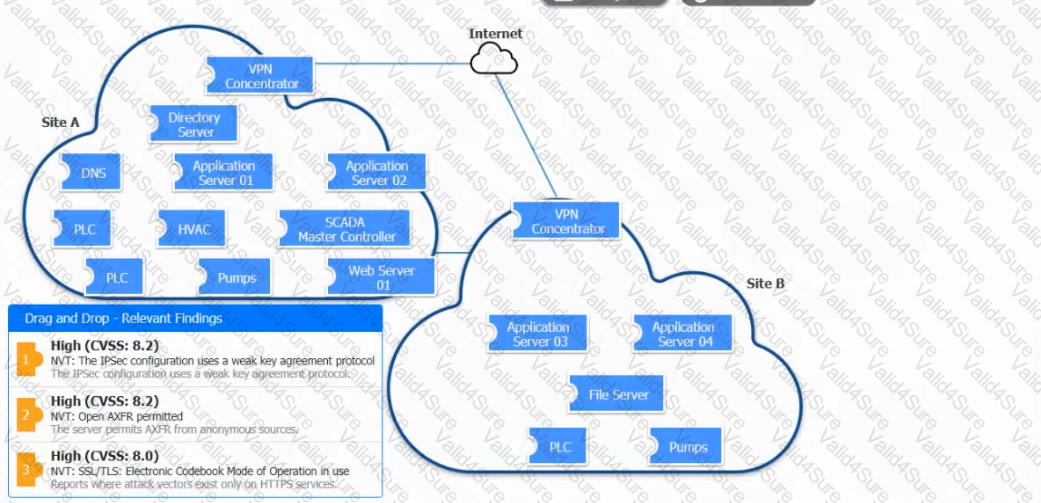
A vulnerability scan with the latest definitions was performed across Sites A and B.
Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
A company has a DLP system with the following capabilities:
• Text examination
• Optical character recognition
• File type validation
• Multilingual translation of key words and phrases
• Blocking of content encrypted with a known cipher
• Examination of all egress points
Despite the existing protections a malicious insider was able to exfilltrated confidential information DLP logs show the malicious insider transferred a number of JPEG files to an external host but each of those files appears as negative for the presence of confidential information. Which of the following are the MOST likely explanations for this issue? (Select TWO)
An ICS security engineer is performing a security assessment at a bank in Chicago. The engineer reviews the following output:

Which of the following tools is the engineer using the provide this output?
A small company is implementing a new technology that promises greater performance but does not abide by accepted RFCs. Which of the following should the company do to ensure the risks associated with Implementing the standard-violating technology is addressed?
An organization wishes to implement cloud computing, but it is not sure which service to choose. The organization wants to be able to share Tiles, collaborate, and use applications that are fully managed on a private network. Which of the following types of cloud computing services should the organization implement based on its needs?
A financial institution has several that currently employ the following controls:
* The severs follow a monthly patching cycle.
* All changes must go through a change management process.
* Developers and systems administrators must log into a jumpbox to access the servers hosting the data using two-factor authentication.
* The servers are on an isolated VLAN and cannot be directly accessed from the internal production network.
An outage recently occurred and lasted several days due to an upgrade that circumvented the approval process. Once the security team discovered an unauthorized patch was installed, they were able to resume operations within an hour. Which of the following should the security administrator recommend to reduce the time to resolution if a similar incident occurs in the future?
A company recently developed a new mobile application that will be used to access a sensitive system. The application and the system have the following requirements:
• The application contains sensitive encryption material and should not be accessible over the network
• The system should not be exposed to the Internet
• Communication must be encrypted and authenticated by both the server and the client
Which of the following can be used to install the application on the mobile device? (Select TWO).
A consultant is planning an assessment of a customer-developed system. The system consists of a custom-engineered board with modified open-source drivers and a one-off management GUI The system relies on two- factor authentication for interactive sessions, employs strong certificate-based data-in-transit encryption, and randomly switches ports for each session. Which of the following would yield the MOST useful information'?