CAS-003 Exam Dumps - CompTIA Advanced Security Practitioner (CASP) Exam
A developer is writing a new mobile application that employees will use to connect to an Internet-facing sensitive system The security team is concerned with MITM attacks against the encrypted application traffic aimed at intercepting and decrypting sensitive information from the server to the mobile client. Which of the following should the developer implement to address the security team's concerns? (Select TWO).
An analyst is testing the security of a server and attempting to infiltrate the network. The analyst is able to obtain the following output after running some tools on the server.
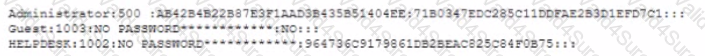
Which of the following will the analyst most likely do NEXT?
A security engineer needs (o implement controls that will prevent the theft of data by insiders who have valid credentials Recent modems were earned out with mobile and wearable devices that were used as transfer vectors In response USB data transfers are now tightly controlled and require executive authorization Which of the following controls will further reduce the likelihood of another data theft?
A product owner is working w*h a security engineer to improve the security surrounding certificate revocation which is important for the clients using a web application. The organization is currently using a CRL configuration to manage revocation, but it is looking for a solution that addresses the reporting delays associated with CRLs. The security engineer recommends OCSP but the product owner is concerned about the overhead associated with its use Which of the following would the security engineer MOST likely suggest to address the product owner's concerns?
Employees who travel internationally have been issued corporate mobile devices When traveling through border security employees report border police officers have asked them to power on and unlock the* phones and tablets for inspection Non-compliance with these requests may lead to the devices being confiscated After the phones have been unlocked, the police connect them to laptops for several minutes The company rs concerned about potential exposure of IP financial data or other sensitive information Which of the following is MOST likely to protect the company's data m future situations''
Company policy mandates the secure disposal of sensitive data at the end of the useful lifespan of IT equipment. The IT department donates old devices to charity and recycles truly obsolete equipment In addition to deleting workstations from the systems responsible for monitoring network connections which of the following actions should the company implement? (Select TWO)
A company has decided to move an ERP application to a public cloud vendor. The company wants to replicate some of its global policies from on premises to cloud. The policies include data encryption, token management, and limited user access to the ERP application. The Chief Information Officer (CIO) is mainly concerned about privileged accounts that might be compromised and used to alter data in the ERP application. Which of the following is the BEST option to meet the requirements?
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership. Which of the follow would MOST likely be used?