CRISC Exam Dumps - Certified in Risk and Information Systems Control
Which of the following s MOST likely to deter an employee from engaging in inappropriate use of company owned IT systems?
Which of the following BEST enables a risk practitioner to understand management's approach to organizational risk?
Which of the following is the BEST approach for an organization in a heavily regulated industry to comprehensively test application functionality?
An organization is considering outsourcing user administration controls tor a critical system. The potential vendor has offered to perform quarterly sett-audits of its controls instead of having annual independent audits. Which of the following should be of GREATEST concern to me risk practitioner?
Senior management is deciding whether to share confidential data with the organization's business partners. The BEST course of action for a risk practitioner would be to submit a report to senior management containing the:
Which of the following is MOST important for successful incident response?
An organization's recovery team is attempting to recover critical data backups following a major flood in its data center. However, key team members do not know exactly what steps should be taken to address this crisis. Which of the following is the MOST likely cause of this situation?
The following is the snapshot of a recently approved IT risk register maintained by an organization's information security department.
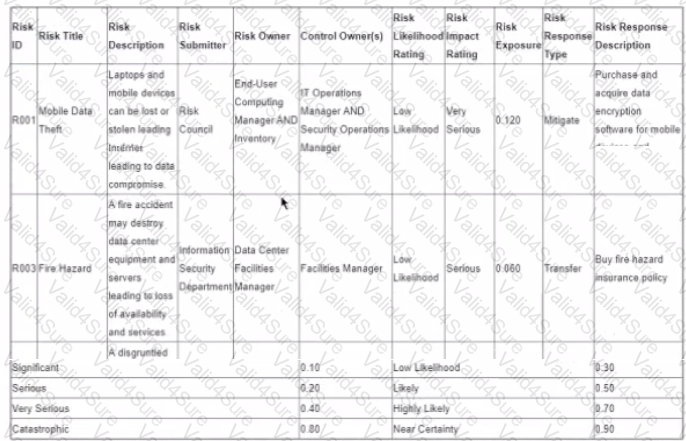
After implementing countermeasures listed in ‘’Risk Response Descriptions’’ for each of the Risk IDs, which of the following component of the register MUST change?