FCP_FGT_AD-7.4 Exam Dumps - FCP - FortiGate 7.4 Administrator
Refer to the exhibits.
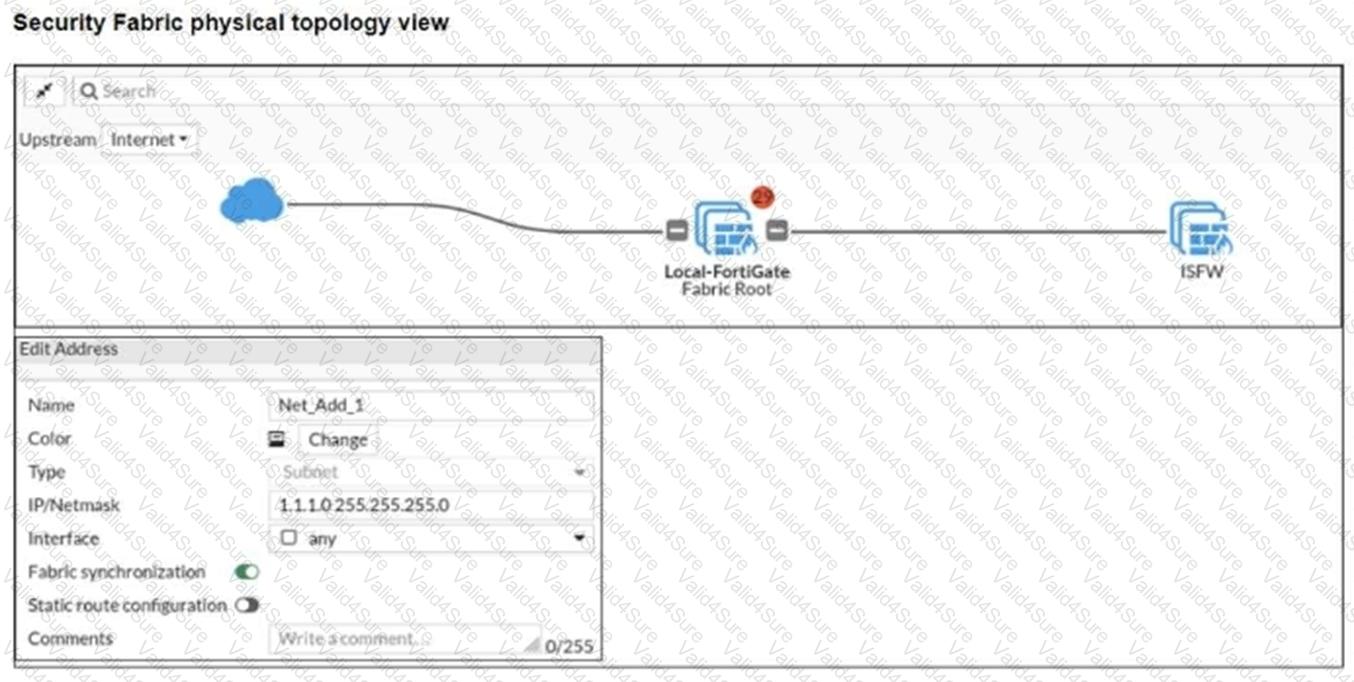
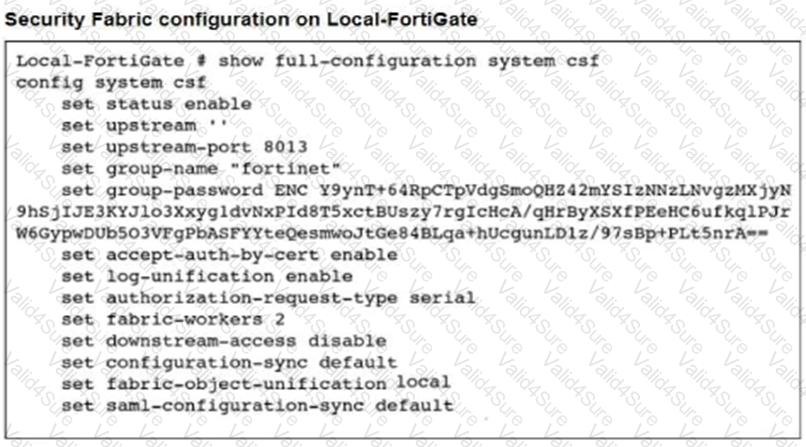

An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
An administrator manages a FortiGate model that supports NTurbo.
How does NTurbo enhance performance for flow-based inspection?
Refer to the exhibit, which shows the IPS sensor configuration.
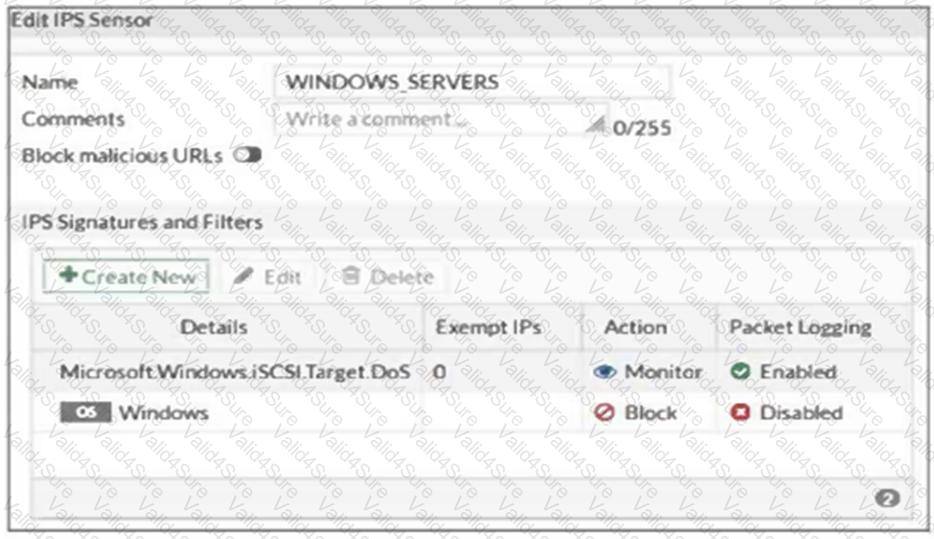
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Refer to the exhibit.
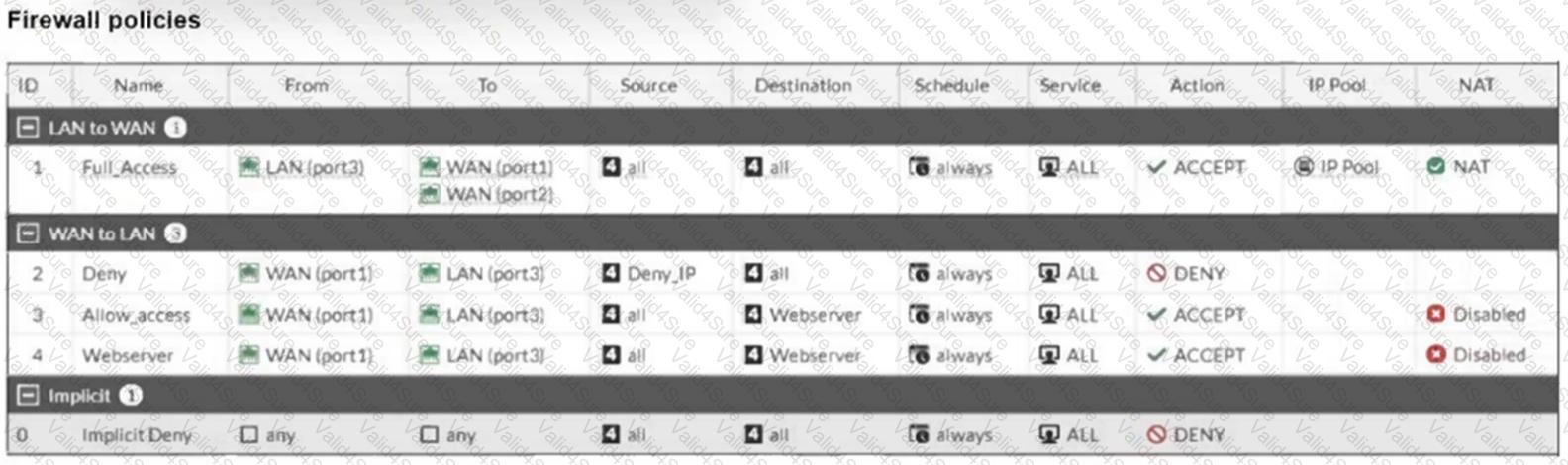
Which statement about this firewall policy list is true?
A FortiGate administrator is required to reduce the attack surface on the SSL VPN portal.
Which SSL timer can you use to mitigate a denial of service (DoS) attack?