FCP_FGT_AD-7.4 Exam Dumps - FCP - FortiGate 7.4 Administrator
Refer to the exhibit.
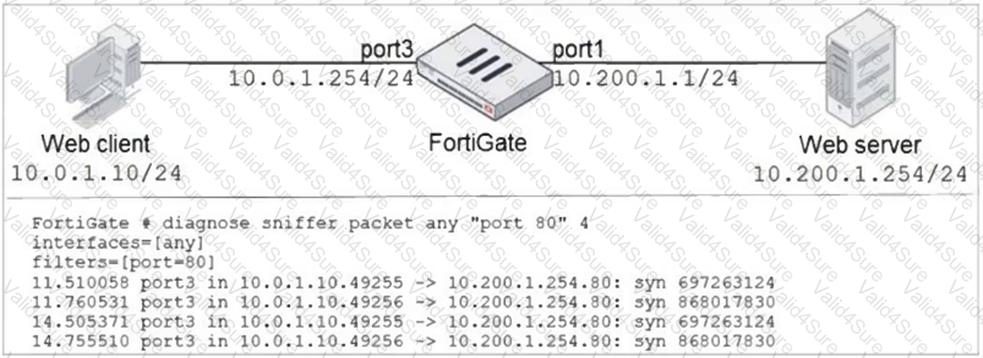
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Which method allows management access to the FortiGate CLI without network connectivity?
Refer to the exhibits, which show the firewall policy and an antivirus profile configuration.
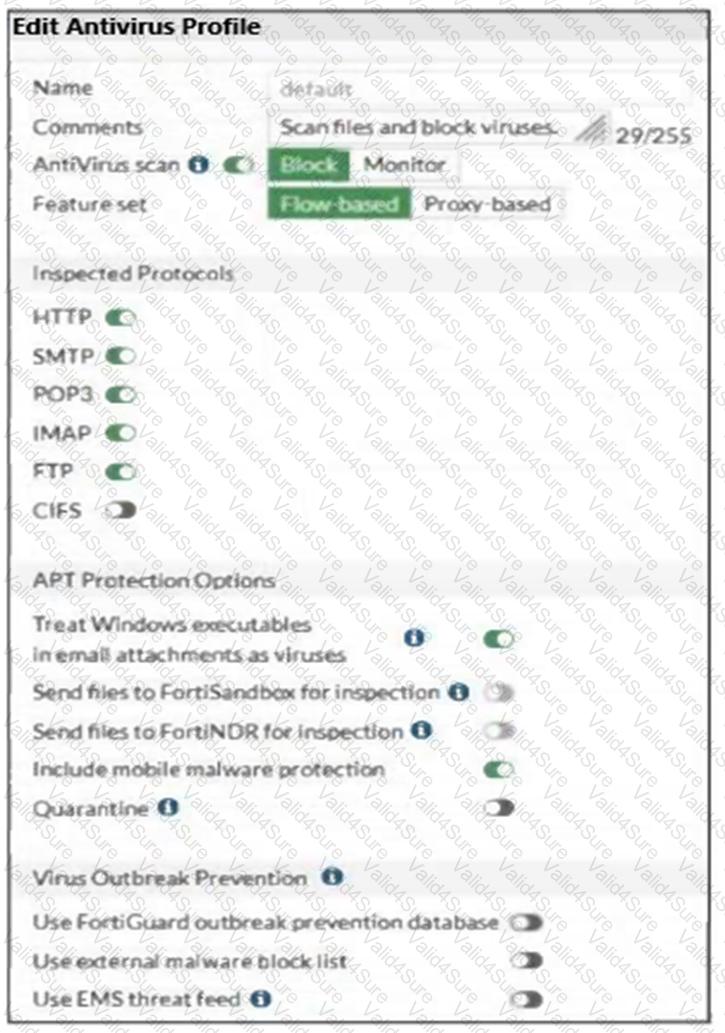
Why is the user unable to receive a block replacement message when downloading an infected file for the first time?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
FortiGate is integrated with FortiAnalyzer and FortiManager.
When a firewall policy is created, which attribute is added to the policy to improve functionality and to support recording logs to FortiAnalyzer or FortiManager?