H12-261_V3.0 Exam Dumps - HCIE-Routing & Switching (Written) V3.0
The association between LDP and IGP means that IGP suppresses the advertisement of reachable routes to ensure that LDP and IGP cooperate to complete network convergence, so that IGP and LDP maintain the same path, minimize traffic loss, and improve the reliability of the entire network.
an engineer uses 2 router for IPv46 business test, by running BGP4+Simulate the interconnection between headquarters and branches. The network logical topology is shown in the figure, about the IPv6 between the two devices Route delivery, which of the following statements is false?

If the advertised route entry is deleted on the BGP router, the BGP router will be triggered to send an Update message for route revocation. Well-known mandatory attribute with revoked routing entries.
What command can be used to prevent users from accessing multiple devices through the HUB on the access port of the switch? (Single Choice)
The two routers are connected together through serial ports, but they cannot ping each other. Now check the port status as follows:
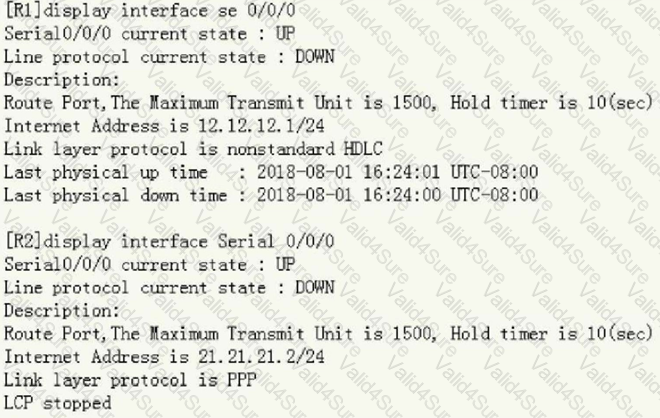
Can you determine the cause from the above information?
The OSPFv3 protocol is a separately developed protocol. It is somewhat different from OSPFv2. Regarding OSPFv3 is based on links rather than network segments, which of the following statements is wrong?
IPSG can statically configure the binding table, orDHCP-Snooping is used together to form a binding table