Note! Following H12-261_V3.0 Exam is Retired now. Please select the alternative replacement for your Exam Certification.
H12-261_V3.0 Exam Dumps - HCIE-Routing & Switching (Written) V3.0
Question # 4
In an MPLS BGP VPN network without the MPLS penultimate hop popping technology enabled, when a packet arrives at the last hop PE, the packet has two layers of labels, and the two layers of labels can be the same.
Question # 5
In the topology shown in the figure, if the entire network runs OSPFv3 without importing external routes, what type of LSA will not be generated on R1?
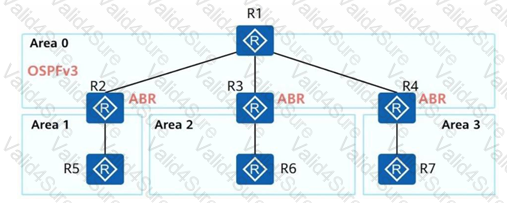
Question # 6
In the campus network, what are the problems of manually creating static tunnels?
Question # 7
The following are about 802.1x authentication. What are the correct statements about RADIUS authentication and HWTACACS authentication?