NCP-MCI-6.5 Exam Dumps - Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI) v6.5 exam
An administrator has been tasked with increasing security on Nutanix cluster by disabling password authentication when accessing the CVM and AHV hosts and instead moving to key-based SSH,
What is the easiest way for the administrator to meet these needs?
A two-node ROBO cluster is configured with a witness VM.
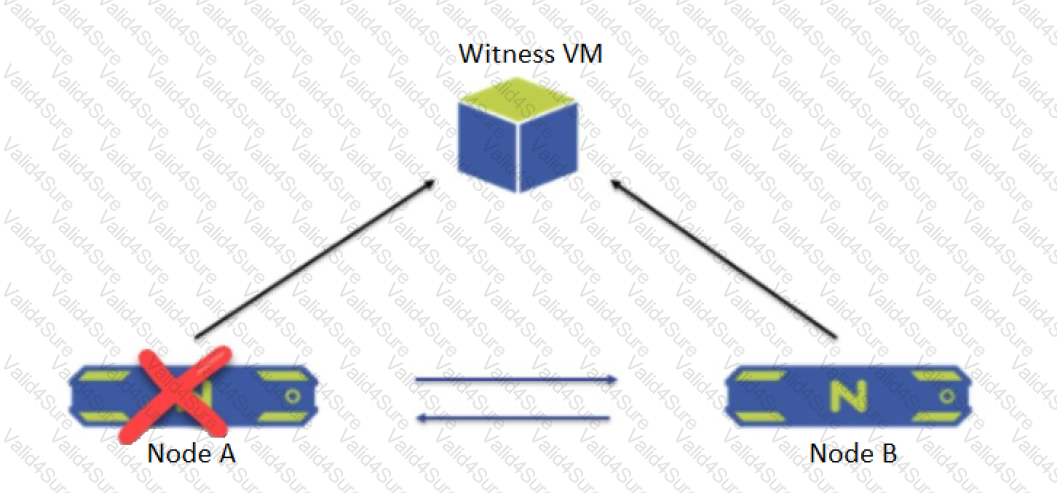
What happens when Node A goes down?
A system administrator needs to add more VMs to their Nutanix cluster.
Which two actions should the administrator perform to determine if the current cluster can accommodate the new VMs? (Choose two)
A vDisk is read by multiple VMs. The cluster creates immutable copies of the vDisk. What are these vDisk copies called?
Which two methods are available when migrating a VM from a legacy 3-tier solution using VMware ESXi to AHV? (Choose two.)
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
In the event of a disk failure, which process will immediately ad automatically scans Cassandra to find all data previously hosted on the failed disk, and all disks in that node?
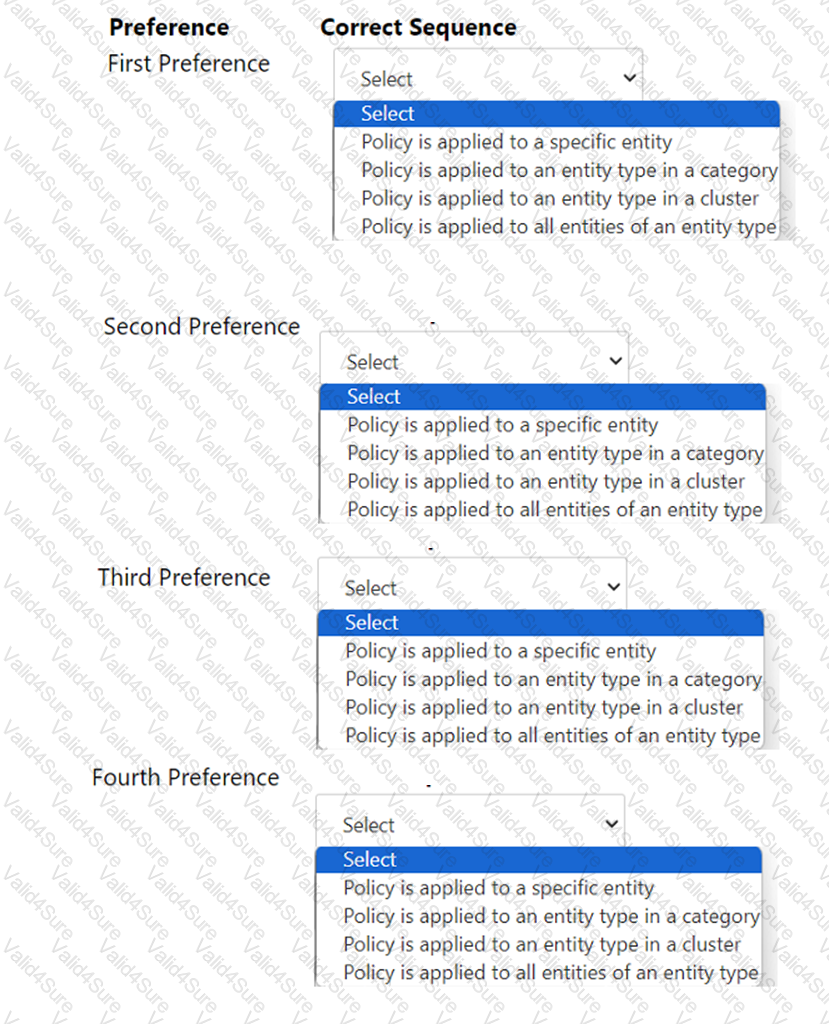
An administrator has created several custom alert policies, which are applied to the same entities. Prism Central displays a message that a similar policy exists.
In what order of precedence are overlapping policies evaluated?