NCP-MCI-6.5 Exam Dumps - Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI) v6.5 exam
Question # 6
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
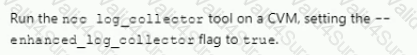
C)

D)

Question # 7
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
Question # 8
Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)