NSE4_FGT-7.2 Exam Dumps - Fortinet NSE 4 - FortiOS 7.2
84
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
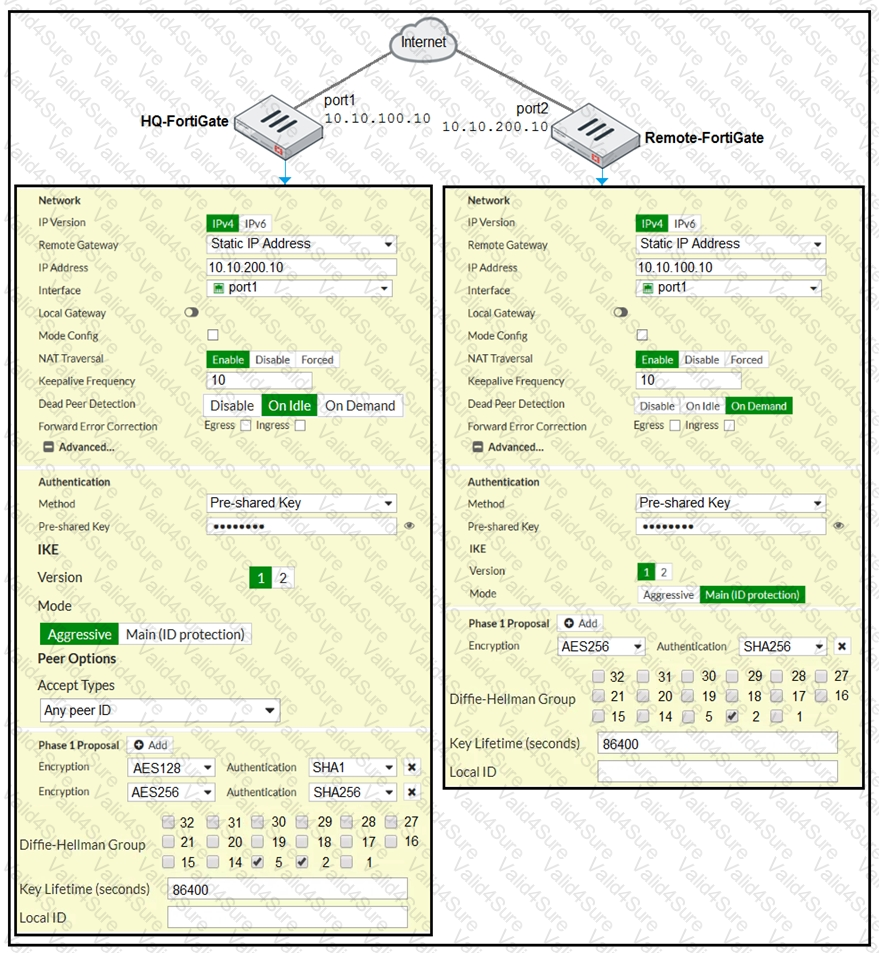
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
Refer to the exhibit.
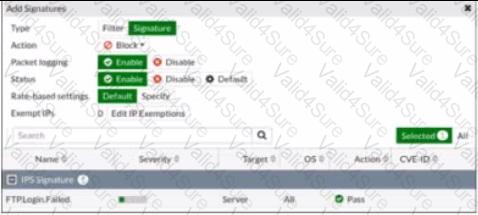
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
An administrator is running the following sniffer command:
Which three pieces of Information will be Included in me sniffer output? {Choose three.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
Refer to the exhibits.
The exhibits show a network diagram and firewall configurations.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2. Remote-User1 must be able to access the Webserver. Remote-User2 must not be able to access the Webserver.
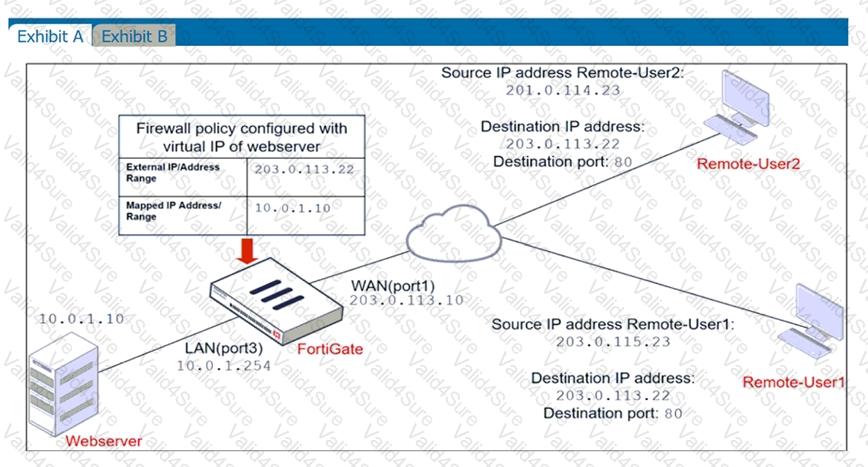
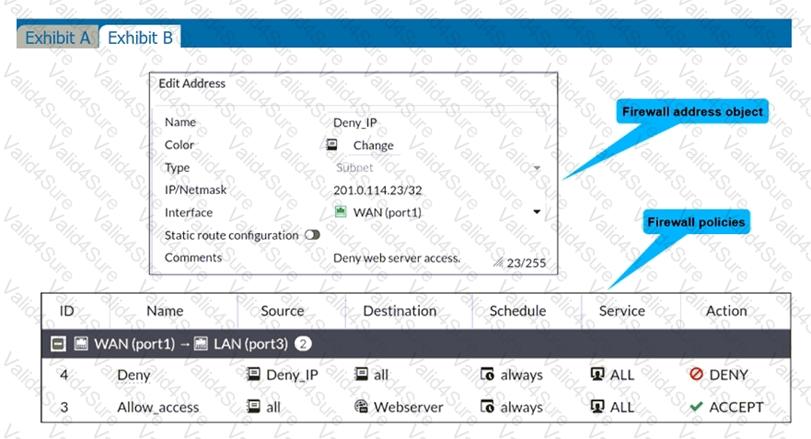
In this scenario, which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)