NSE4_FGT-7.2 Exam Dumps - Fortinet NSE 4 - FortiOS 7.2
Searching for workable clues to ace the Fortinet NSE4_FGT-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE4_FGT-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
94
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
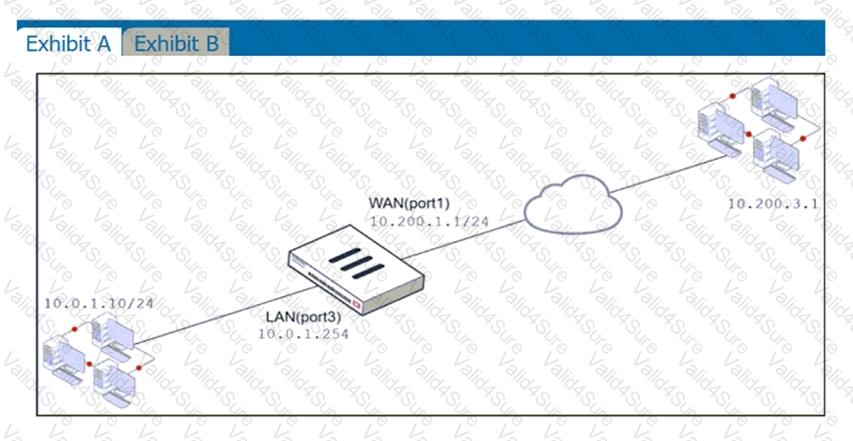
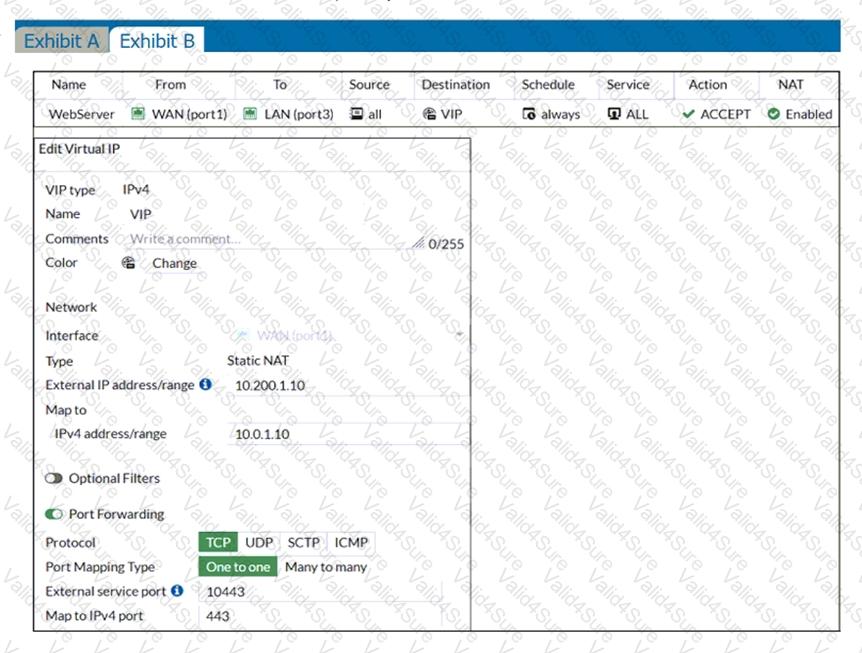
If the host 10.200.3.1 sends a TCP SYN packet on port 10443 to 10.200.1.10, what will the source address, destination address, and destination port of the packet be, after FortiGate forwards the packet to the destination?
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
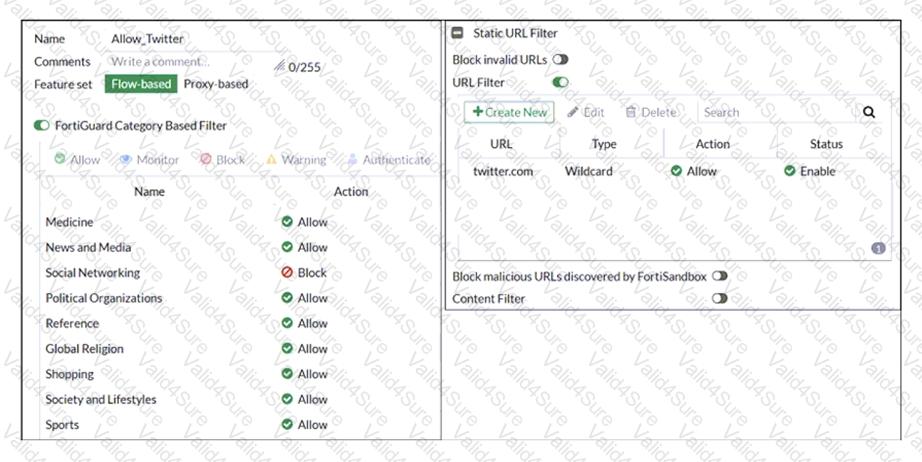
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
Refer to the web filter raw logs.
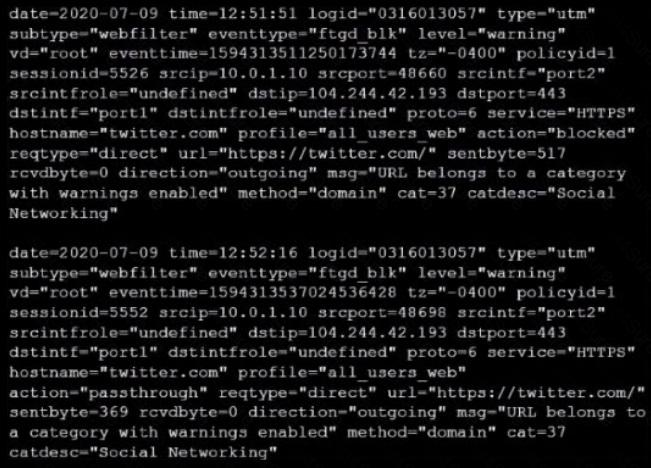
Based on the raw logs shown in the exhibit, which statement is correct?
Refer to the exhibit.
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
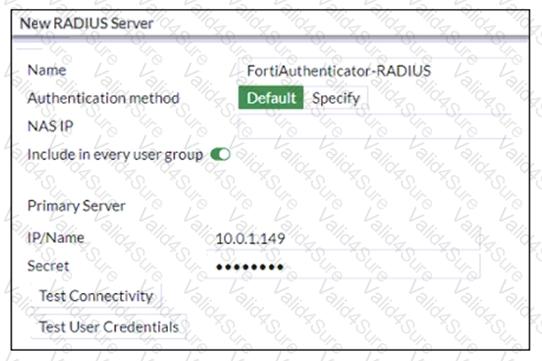
What is the impact of using the Include in every user group option in a RADIUS configuration?
An administrator wants to configure timeouts for users. Regardless of the userTMs behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?