NSE4_FGT-7.2 Exam Dumps - Fortinet NSE 4 - FortiOS 7.2
Refer to the exhibit.
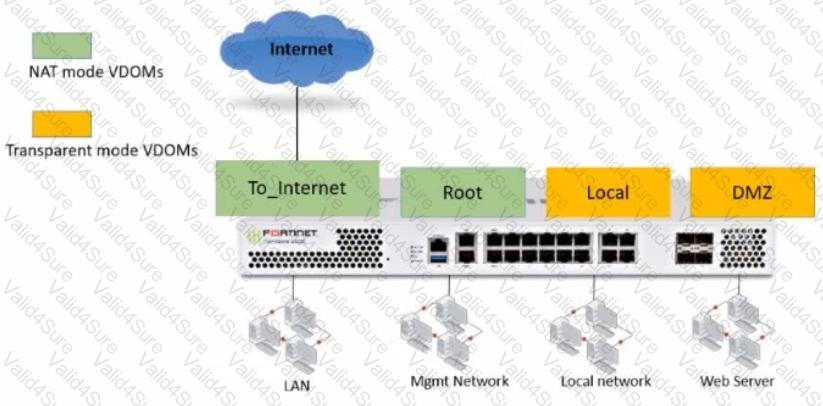
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem .
With this configuration, which statement is true?
Refer to the exhibit.
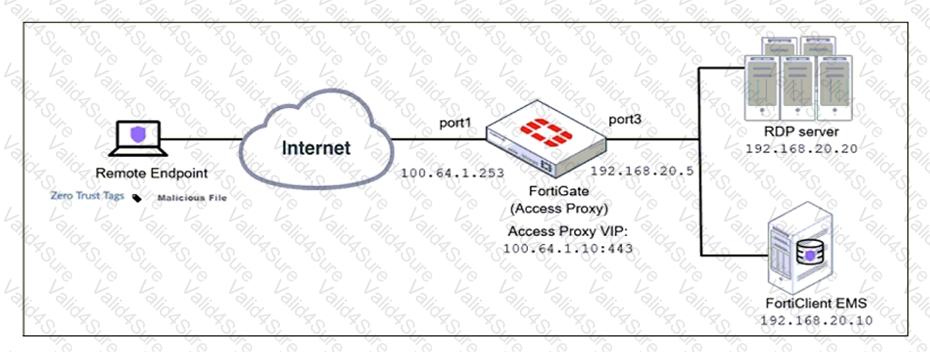
Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
49
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
What type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
Refer to the exhibit showing a debug flow output.

What two conclusions can you make from the debug flow output? (Choose two.)
By default, FortiGate is configured to use HTTPS when performing live web filtering with FortiGuard servers.
Which CLI command will cause FortiGate to use an unreliable protocol to communicate with FortiGuard servers for live web filtering?