NSK200 Exam Dumps - Netskope Certified Cloud Security Integrator (NCCSI)
Your customer is using a virtual desktop infrastructure (VDI) for their support engineers. Multiple users will be logging into the same device, and they want to detect activities for each user.
You are deploying a Netskope client in your corporate office network. You are aware of firewall or proxy rules that need to be modified to allow traffic.
Which two statements are true in this scenario? (Choose two.)
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
Review the exhibit.
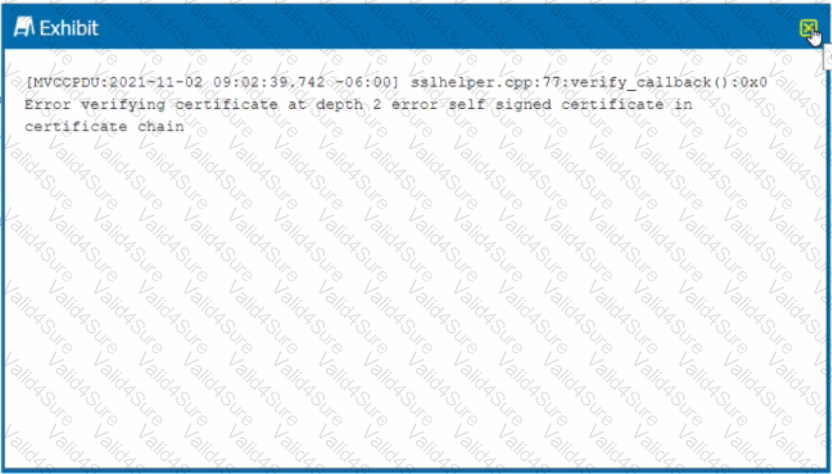
While diagnosing an NPA connectivity issue, you notice an error message in the Netskope client logs.
Referring to the exhibit, what does this error represent?
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?
You want to secure Microsoft Exchange and Gmail SMTP traffic for DLP using Netskope. Which statement is true about this scenario when using the Netskope client?
You are currently migrating users away from a legacy proxy to the Netskope client in the company’s corporate offices. You have deployed the client to a pilot group; however, when the client attempts to connect to Netskope, it fails to establish a tunnel.
In this scenario, what would cause this problem?
You use Netskope to provide a default Malware Scan profile for use with your malware policies. Also, you want to create a custom malware detection profile.
In this scenario, what are two additional requirements to complete this task? (Choose two.)