NSK200 Exam Dumps - Netskope Certified Cloud Security Integrator (NCCSI)
Searching for workable clues to ace the Netskope NSK200 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSK200 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Review the exhibit.
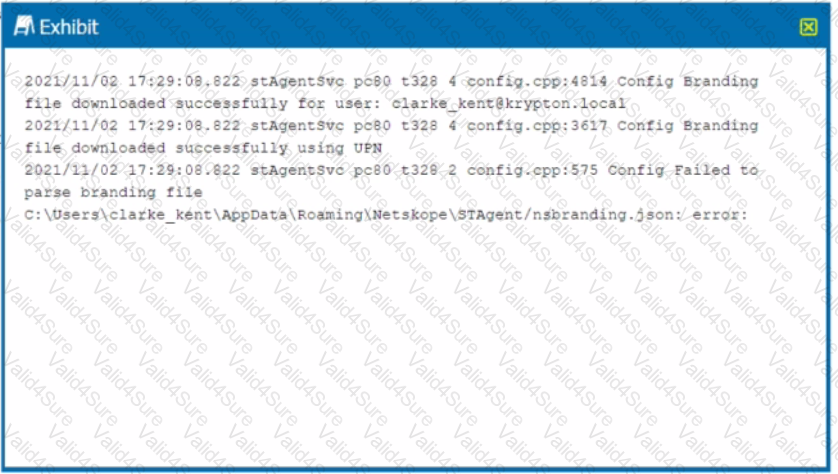
You receive a service request from a user who indicates that their Netskope client is in a disabled state. The exhibit shows an excerpt (rom the affected client nsdebuglog.log.
What is the problem in this scenario?
You discover the ongoing use of the native Dropbox client in your organization. Although Dropbox is not a corporate-approved application, you do not want to prevent the use of Dropbox. You do, however, want to ensure visibility into its usage.
You have deployed a development Web server on a public hosting service using self-signed SSL certificates. After some troubleshooting, you determined that when the Netskope client is enabled, you are unable to access the Web server over SSL. The default Netskope tenant steering configuration is in place.
In this scenario, which two settings are causing this behavior? (Choose two.)
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
Your company wants to know if there has been any unusual user activity. In the UI, you go to Skope IT -> Alerts.
Which two types of alerts would you filter to find this information? (Choose two.)
Review the exhibit.
add log-upload syslogng parserconfig set log-upload syslogng parserconfig 0
logsource <</b>log-source>
You are asked to deploy a virtual appliance OPLP to accept syslog messages directly from the enterprise Palo Alto Networks firewall. You believe that you have configured the OPLP to accept the firewall logs, yet they are not appearing in Risk Insights. Referring to the exhibit, which parser name would be required to complete the new configuration?
Review the exhibit.
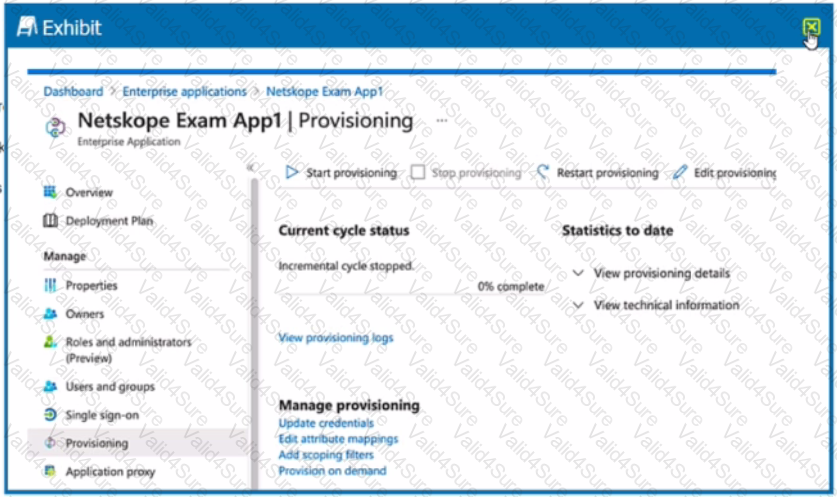
What is the purpose of the configuration page shown Ii the exhibit?
You want to reduce false positives by only triggering policies when contents of your customer database are uploaded to Dropbox. Your maximum database size is 2 MB. In this scenario, what are two ways to accomplish this task? (Choose two.)