NSK200 Exam Dumps - Netskope Certified Cloud Security Integrator (NCCSI)
Searching for workable clues to ace the Netskope NSK200 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSK200 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You are implementing tenant access security and governance controls for privileged users. You want to start with controls that are natively available within the Netskope Cloud Security Platform and do not require external or third-party integration.
Which three access controls would you use in this scenario? (Choose three.)
You are using the Netskope DLP solution. You notice flies containing test data for credit cards are not triggering DLP events when uploaded to Dropbox. There are corresponding page events. Which two scenarios would cause this behavior? (Choose two.)
The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
Review the exhibit.
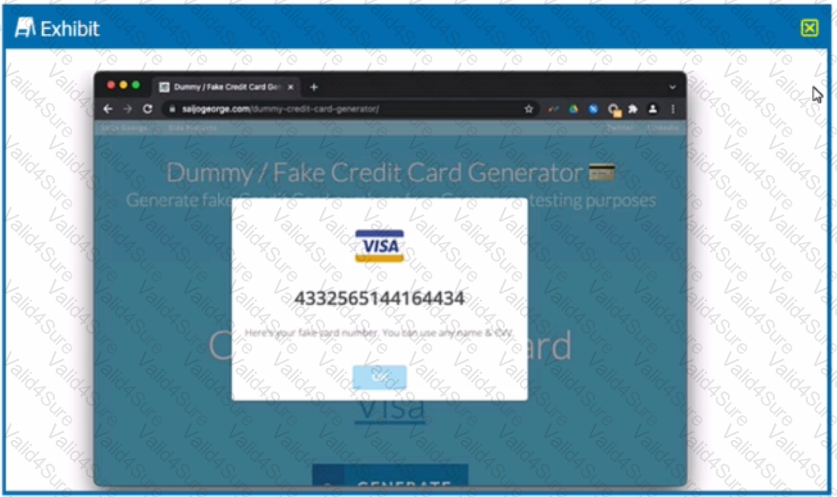
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
Your company needs to keep quarantined files that have been triggered by a DLP policy. In this scenario, which statement Is true?