PEGACPLSA88V1 Exam Dumps - Certified Pega Lead System Architect (CPLSA) Exam 8.8
U+ Bank uses Pega Customer Decision Hubâ„¢ to approve credit card limit changes requested by customers automatically. A scorecard model determines the customer credit score. The automatic approval of credit card limits are processed based on the following criteria set by the bank.
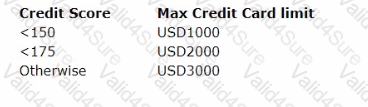
The bank wants to change the threshold value for the USD2000 credit limit from <175 to <200. How do you implement this change?
users complain of difficulty creating a customer service request through facebook massenger. how do you address this issue?
In an e-commerce application that is built on Pega Platform, a data type named Order stores the order-related information. as shown in the following table:
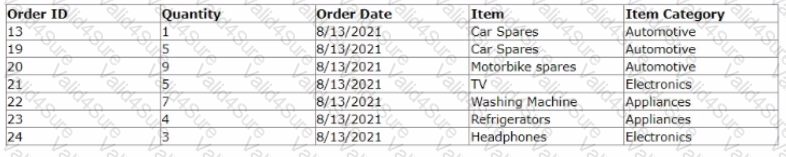
An operations manager wants to view a report at the end of each day. If the number of items ordered in a category is greater than 5, the report displays the number of items in that category that are ordered during the day.
Which option do you use to implement the requirement?
U+ Bank implemented a customer journey for its customers. The journey consists of three stages. The first stage raises awareness about available products, the second stage presents available offers, and in the last stage, customers can talk to an advisor to get a personalized quote. The bank wants to actively increase offers promotion over time.
What action does the bank need to take to achieve this business requirement?
You want to avoid creating unnecessary case-related properties and views. Which three actions do you take to accomplish this goal? (Choose Three)
You are designing a case life cycle to process fraudulent charge claims. After a list of suspected fraudulent charge is submitted, the case advances to the processing stage. In the first step of theprocess fraud claim process, a seprate child case must be created for each suspected fraudulent charge.
After all necessary fraudulent charge cases are created, the parent cse advance to the next step where the customer is notified that their claims are being processed

choose three actions needed to configure the missing step so that a separate child case is created for
each fraudulent charge selected
XYZ Corp requires employees to designate alternate operators to perform their work while they are on vacation. Work vacationing operators should be visible to alternate operators.
How do you configure the application to handle this requirement?
What advantage does a rule-utility-function have over a rule-obj-activity?