PT0-002 Exam Dumps - CompTIA PenTest+ Certification Exam
Searching for workable clues to ace the CompTIA PT0-002 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PT0-002 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following tools provides Python classes for interacting with network protocols?
During an assessment, a penetration tester gathered OSINT for one of the IT systems administrators from the target company and managed to obtain valuable information, including corporate email addresses. Which of the following techniques should the penetration tester perform NEXT?
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client’s IP address. The tester later discovered the SOC had used sinkholing on the penetration tester’s IP address. Which of the following BEST describes what happened?
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
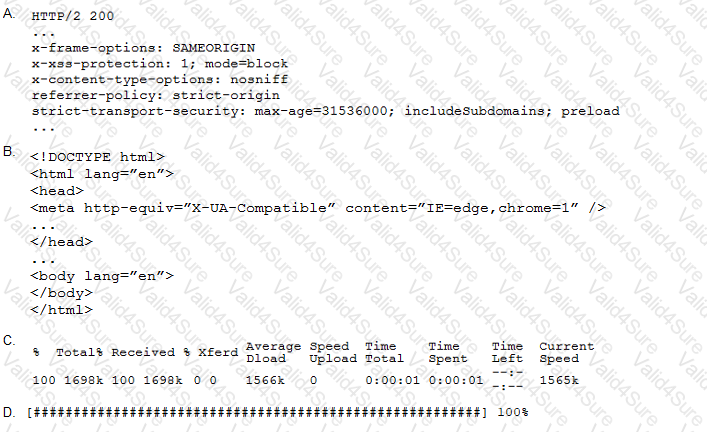
A penetration tester performs the following command:
curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?