PT0-002 Exam Dumps - CompTIA PenTest+ Certification Exam
Searching for workable clues to ace the CompTIA PT0-002 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PT0-002 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
A penetration tester ran the following commands on a Windows server:
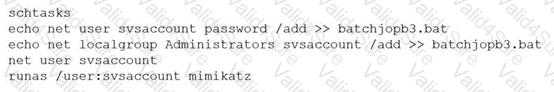
Which of the following should the tester do AFTER delivering the final report?
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?