SY0-701 Exam Dumps - CompTIA Security+ Exam 2025
An organization maintains intellectual property that it wants to protect. Which of the following concepts would be most beneficial to add to the company's security awareness training program?
In which of the following scenarios is tokenization the best privacy technique 10 use?
Which of the following is the best reason to complete an audit in a banking environment?
An administrator finds that all user workstations and servers are displaying a message that is associated with files containing an extension of .ryk. Which of the following types of infections is present on the systems?
Which of the following should a security operations center use to improve its incident response procedure?
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
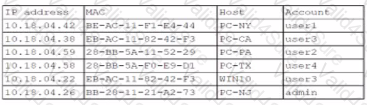
Which of the following is the most likely way a rogue device was allowed to connect?
A systems administrator is changing the password policy within an enterprise environment and wants this update implemented on all systems as quickly as possible. Which of the following operating system security measures will the administrator most likely use?