300-620 Exam Dumps - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
An engineer is extending EPG connectivity to an external network. The external network houses the Layer 3 gateway and other end hosts. Which ACI bridge domain configuration should be used?
An engineer must attach an ESXi host to the Cisco ACI fabric. The host is connected to Leaf 1 and has its gateway IP address 10.10.10.254/24 configured inside the ACI fabric. A new wall is attached to Leaf 2 and mapped to the same EPG and BD as the ESXi host. The engineer must migrate the gateway of the ESXi host to the firewall. Which configuration set complishes this goal?
An engineer is implementing Cisco ACI at a large platform-as-a-service provider using APIC controllers, 9396PX leaf switches, and 9336PQ spine switches. The leaf switch ports are configured as IEEE 802.1p ports. Where does the traffic exit from the EPG in IEEE 802.1p mode in this configuration?
An engineer must implement management policy and data plane separation in the Cisco ACI fabric. Which ACI object must be created in Cisco APIC to accomplish this goal?
The Application team reports that a previously existing port group has disappeared from vCenter. An engineer confirms that the VM domain association for the EPG is no longer present. Which action determines which user is responsible for the change?
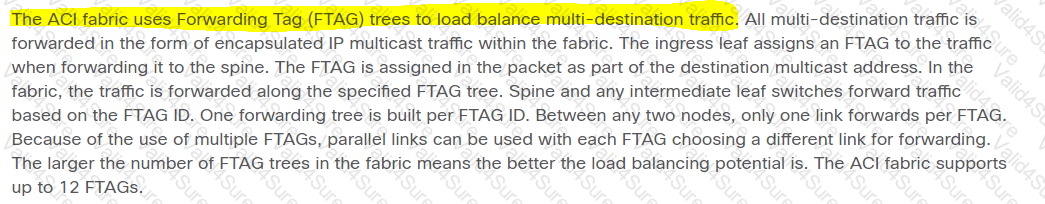
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
Cisco ACI fabric contains a tenant called Prod. User_1 must have write access to tenant Prod and full access to the fabric access policy. Which set of actions must be taken to meet these requirements?