300-620 Exam Dumps - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
Question # 4
When creating a subnet within a bridge domain, which configuration option is used to specify the network visibility of the subnet?
Question # 5
Drag and drop the Cisco ACI filter entry options from the left onto the correct categories on the right indicating what are required or optional parameters.
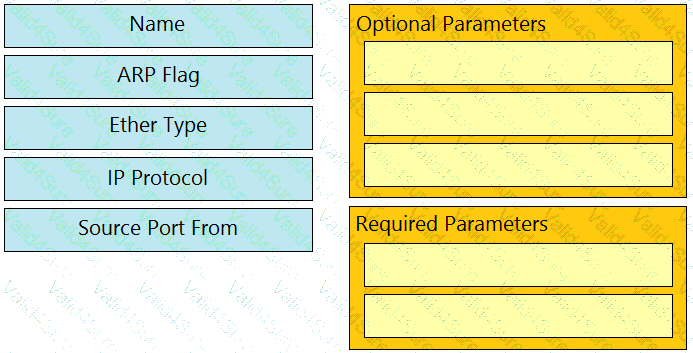
Question # 6
Which two protocols support accessing backup files on a remote location from the APIC? (Choose two.)
Question # 7
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
Question # 8
An engineer deploys a two-pod Cisco ACI Multi-Pod environment. Why should no more than two Cisco APIC controllers be deployed in the same pod?