CTFL-Foundation Exam Dumps - ISTQB Certified Tester Foundation Level
A system calculates the amount of customs duty to be paid:
_ No duty is paid on goods value up to, and including, $2,000.
_ The next $8,000 is taxed at 10%.
_ The next $20,000 after that is taxed at 12%.
_ Any further amount after that is taxed at 17%.
To the nearest $, which of these groups of numbers fall into three DIFFERENT equivalence classes?
Of the following, select the best description of the fundamental test process:
Which of the following would NOT be a typical target of testing support tools?
What content would be in an incident report if that incident report was based on the IEEE 829 Standard for SoftwareTest Documentation?
(i)Identification of configuration items of the software or system.
(ii)Software or system lifecycle process in which the incident was observed.
(iii)Description of the anomaly to enable reproduction of the incident.
(iv)Number of occurrences of the incident.
(v)Classification of the cause of the incident for metrics and for reporting purposes.
Number of correct answers: 1
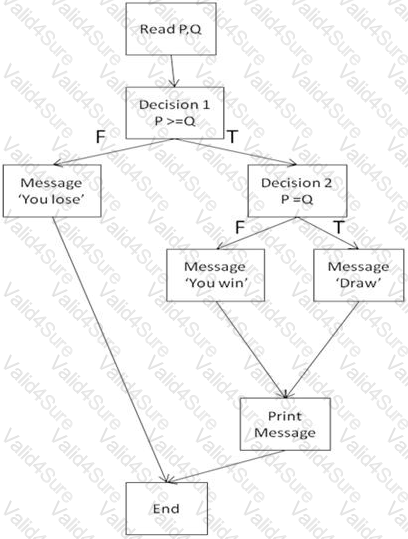
Which of the test cases below will exercise both outcomes from decision 2? [K3]
Refer to the exhibit