N10-009 Exam Dumps - CompTIA Network+ Certification Exam
Network administrators are using the Telnet protocol to administer network devices that are on the 192.168.1.0/24 subnet. Which of the following tools should the administrator use to best identify the devices?
Which of the following connectors allows a singular QSFP transceiver to have several physical connections?
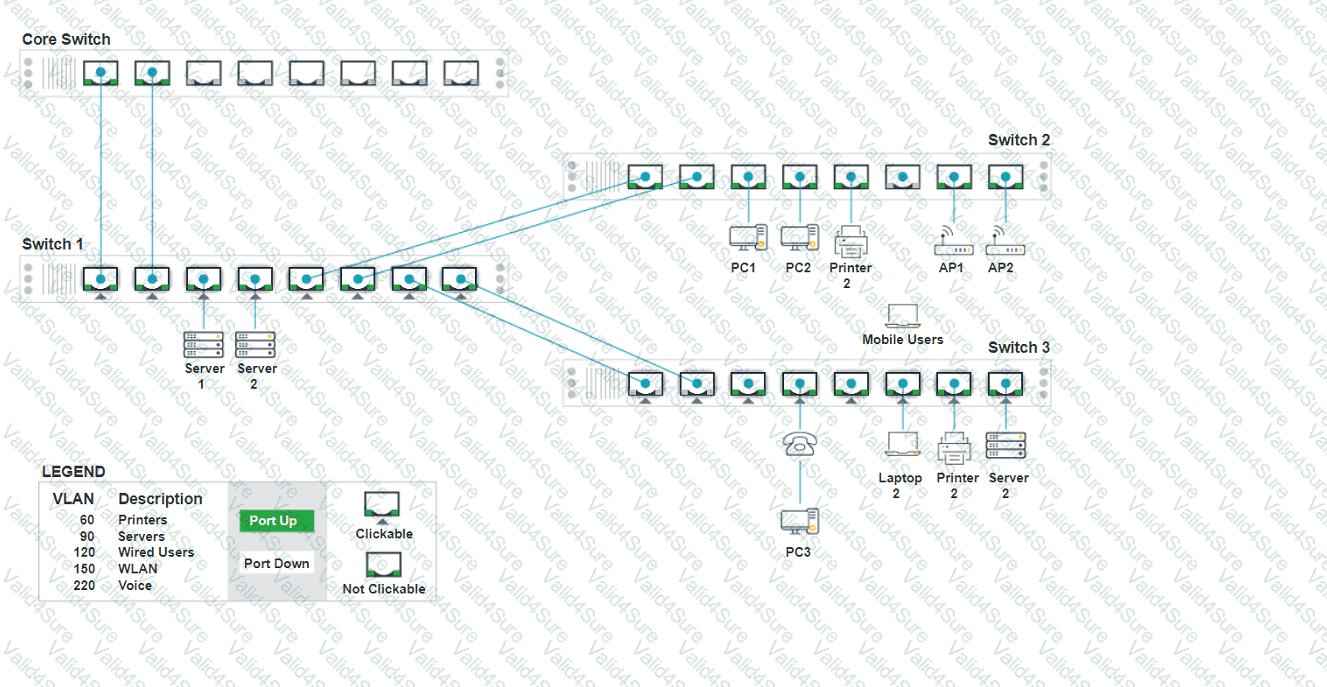
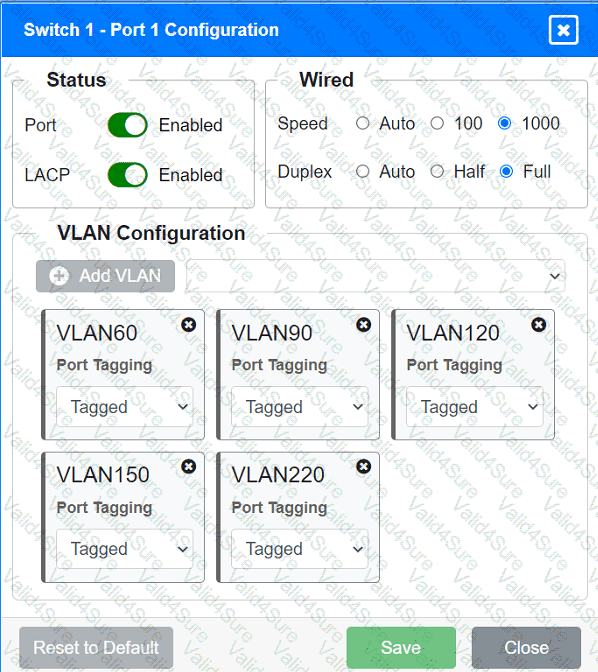
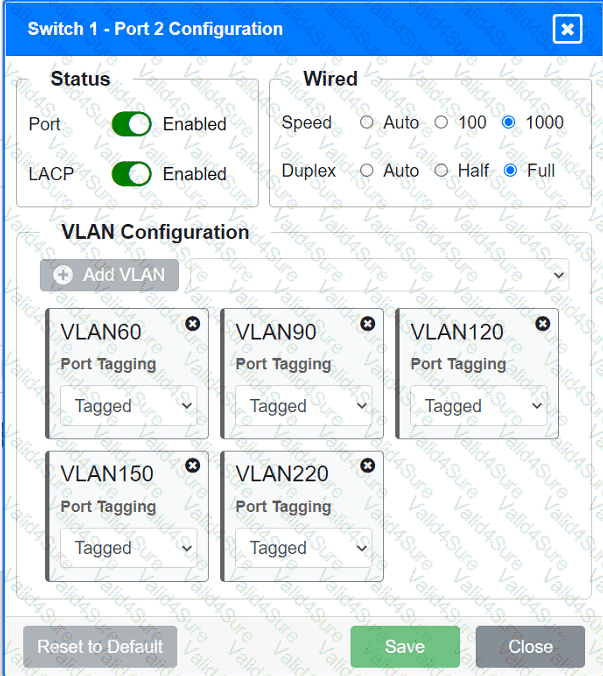
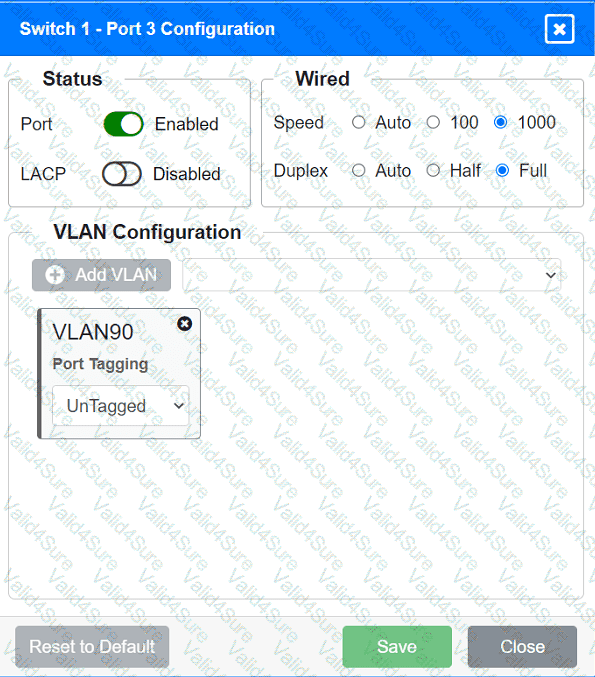
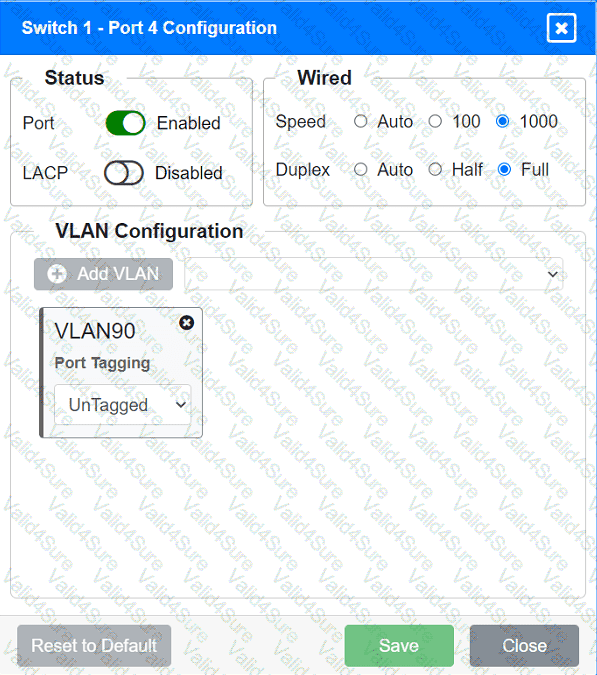
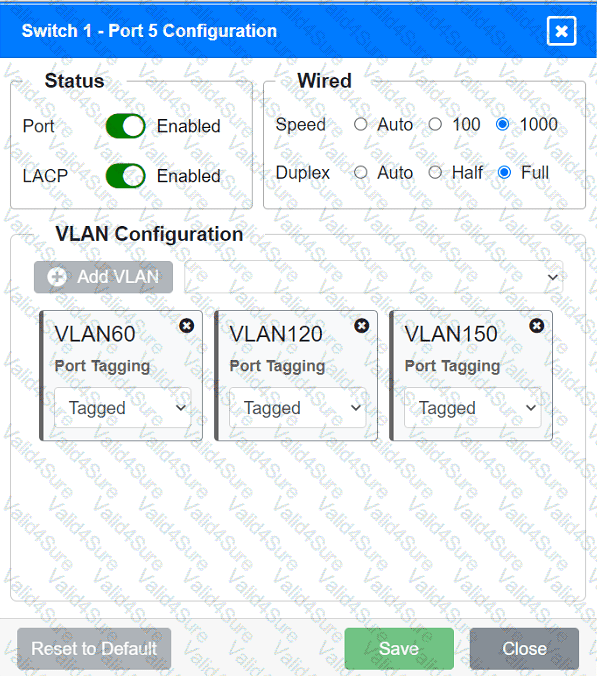
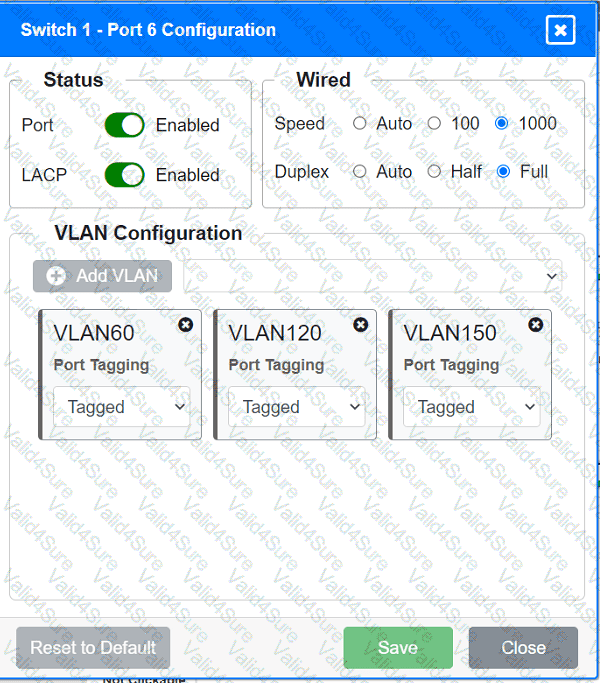
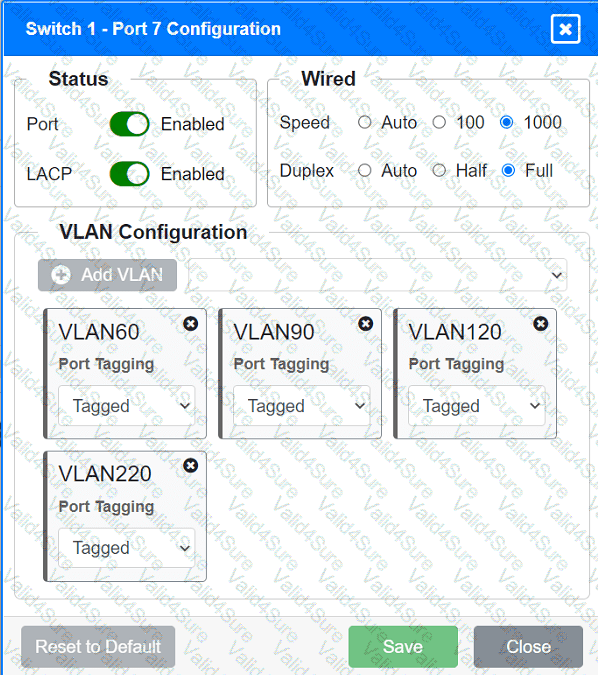
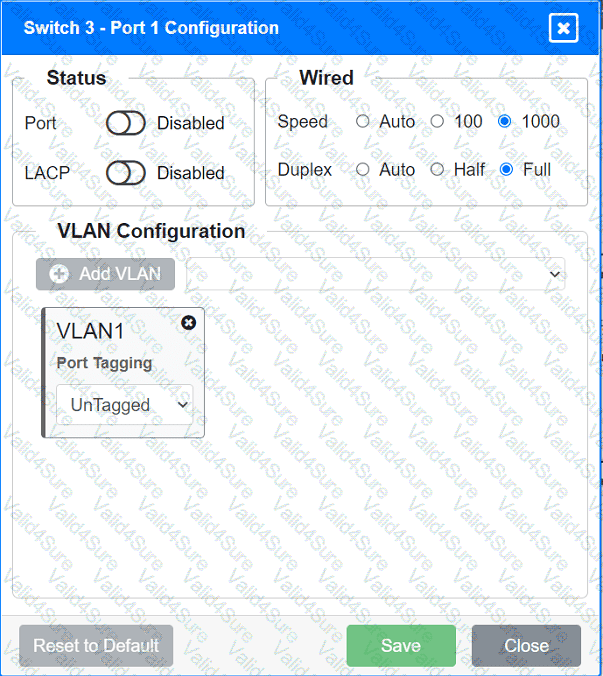
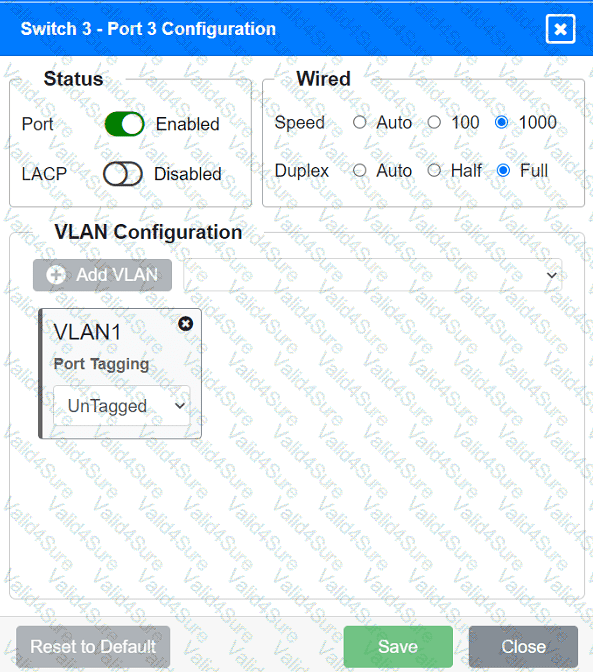
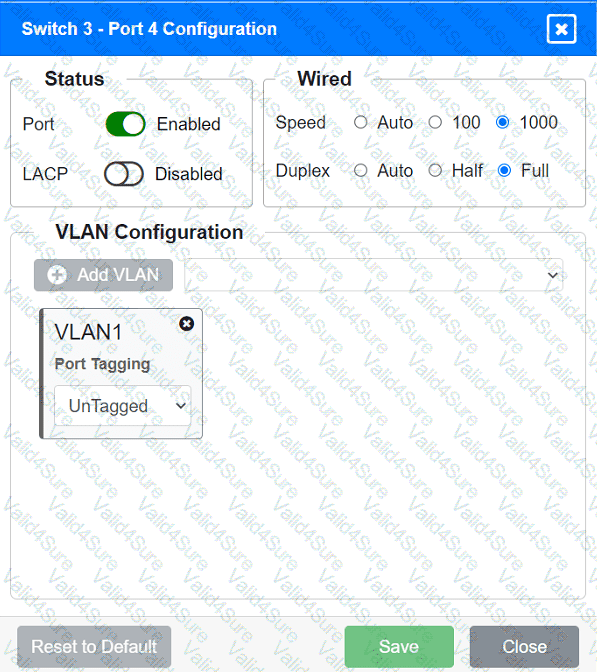
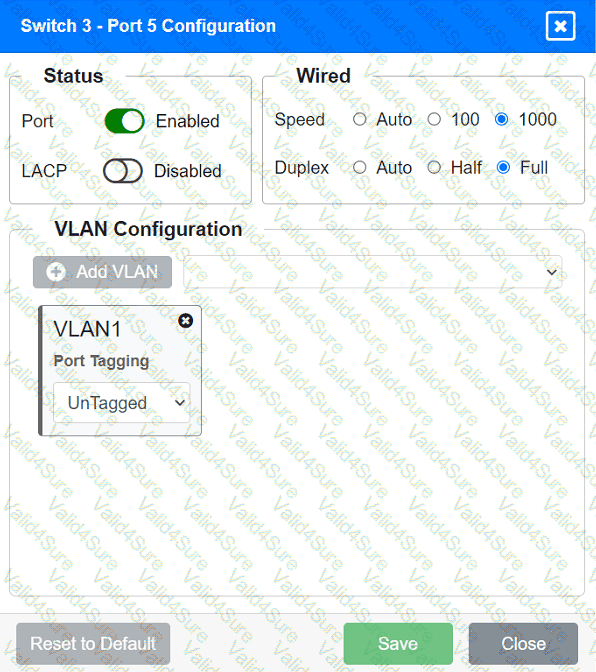
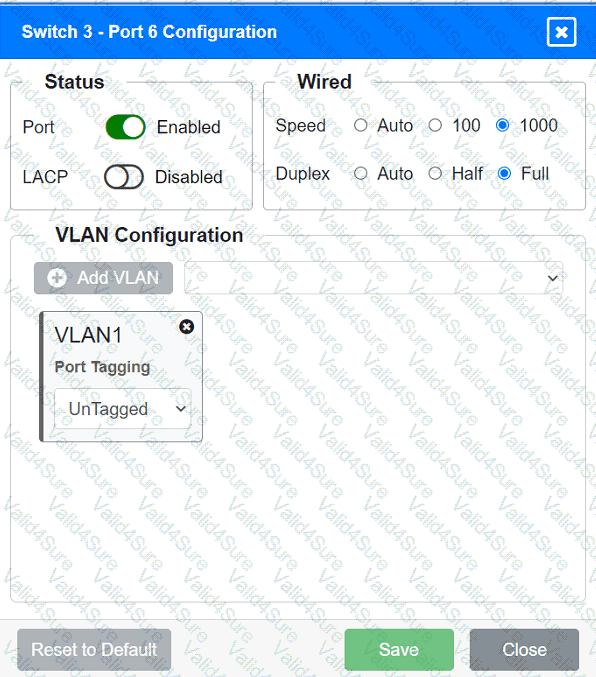
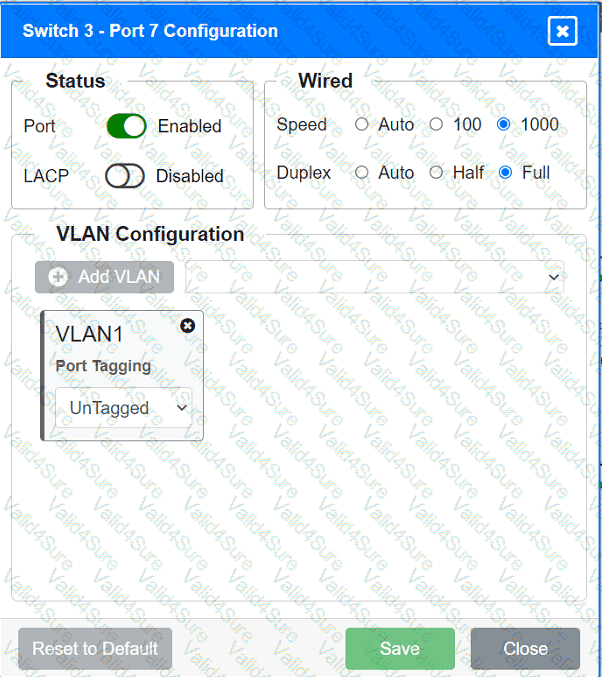
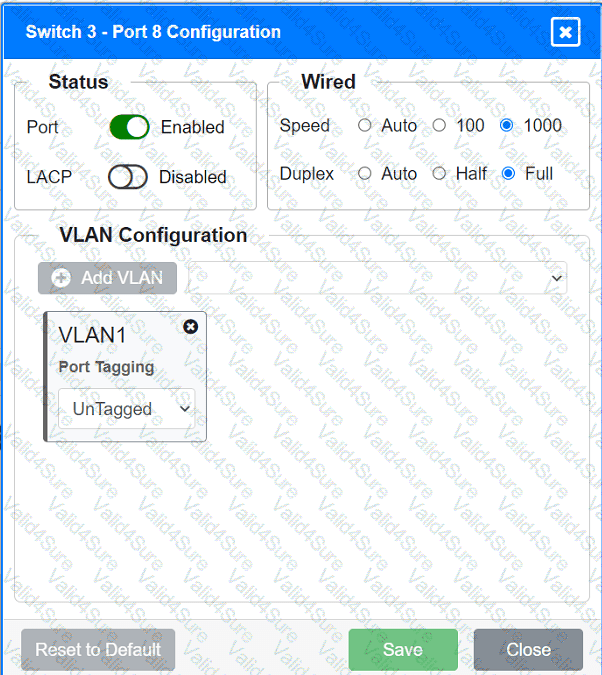
A network technician replaced an access layer switch and needs to reconfigure it to allow the connected devices to connect to the correct networks.
INSTRUCTIONS
Click on the appropriate port(s) on Switch 1 and Switch 3 to verify or reconfigure the
correct settings:
· Ensure each device accesses only its
correctly associated network.
· Disable all unused switchports.
. Require fault-tolerant connections
between the switches.
. Only make necessary changes to
complete the above requirements.

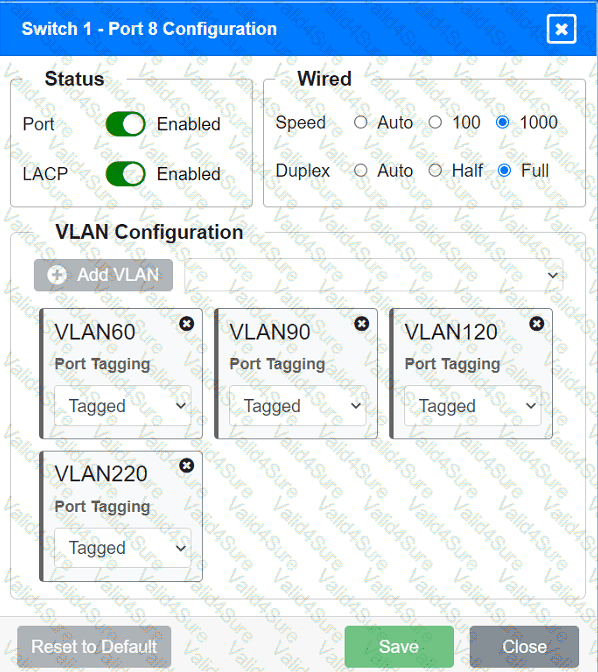
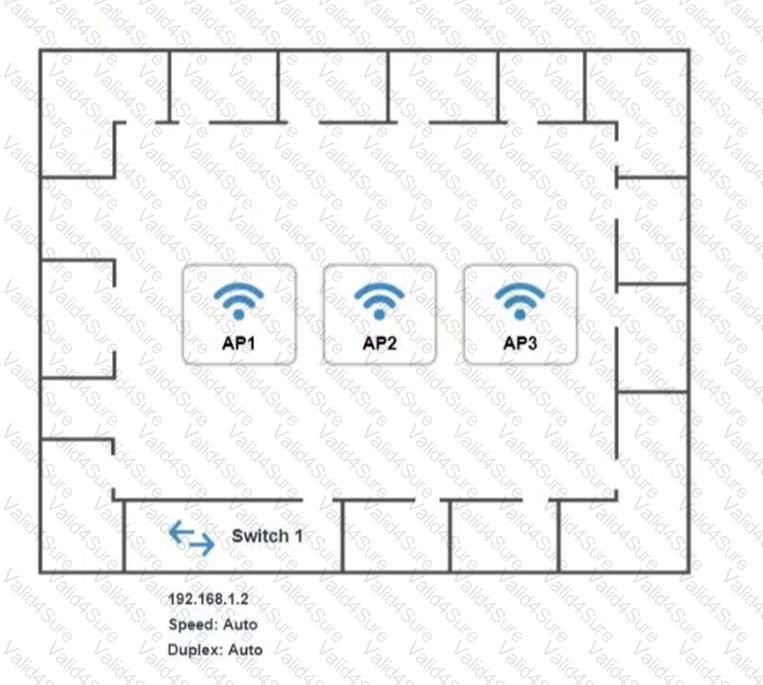
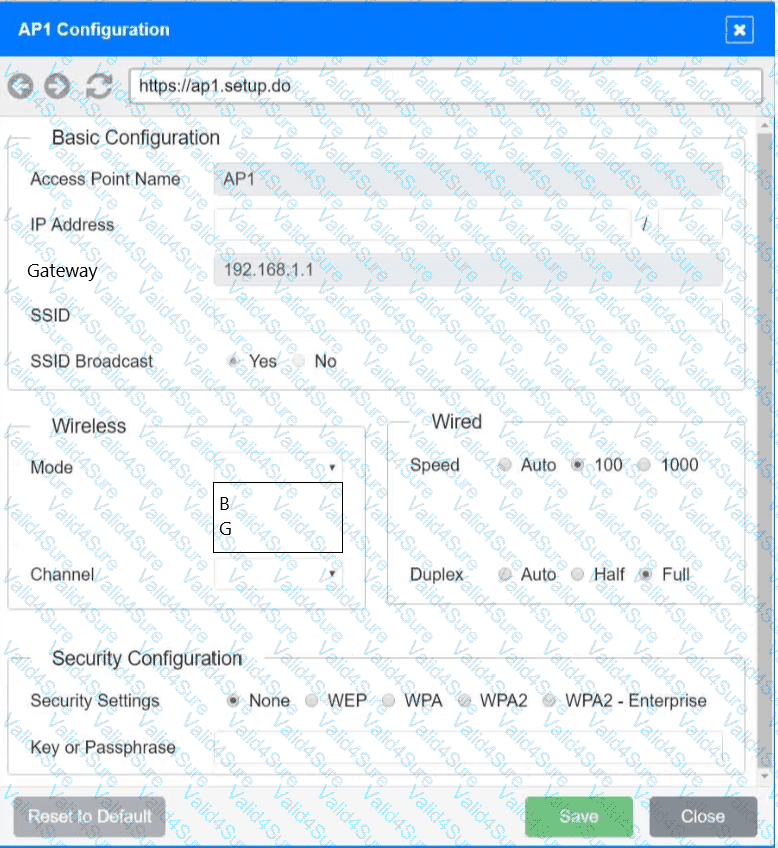
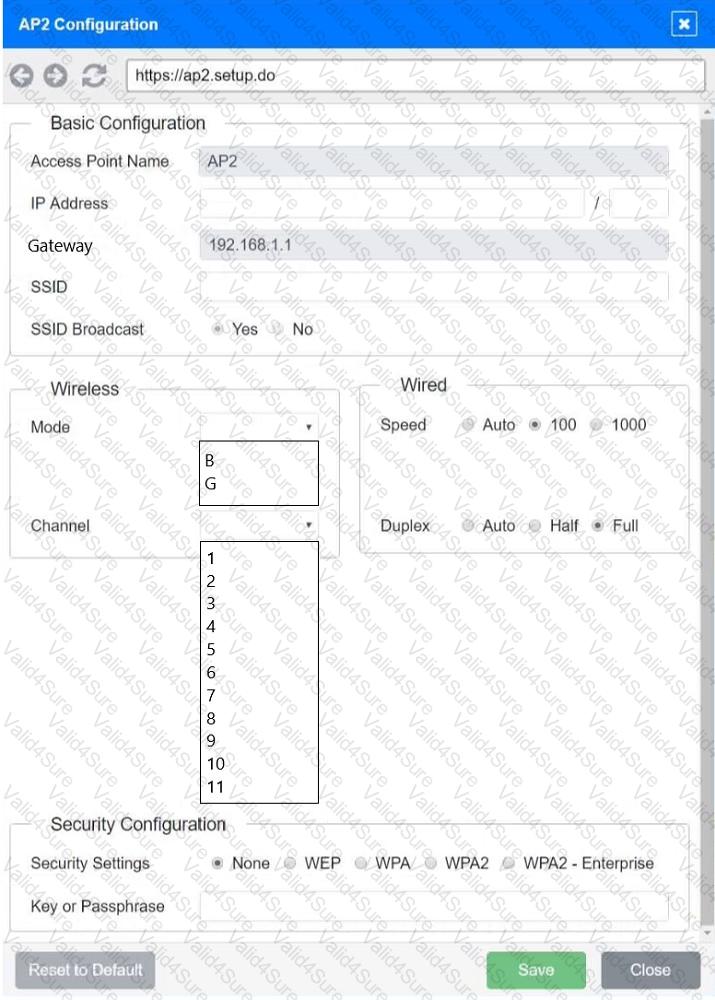
SIMULATION
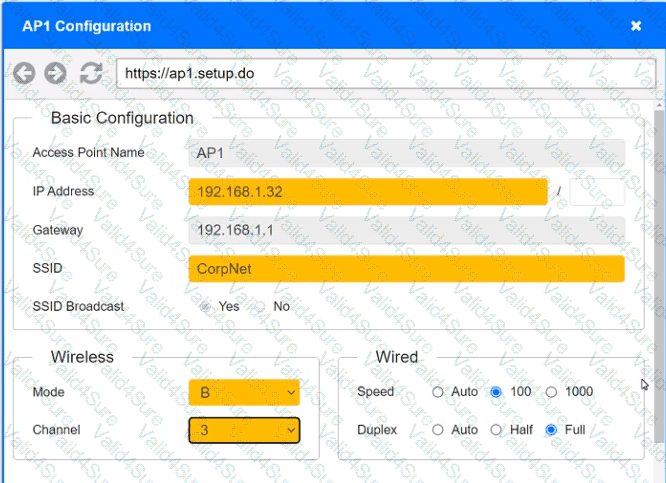
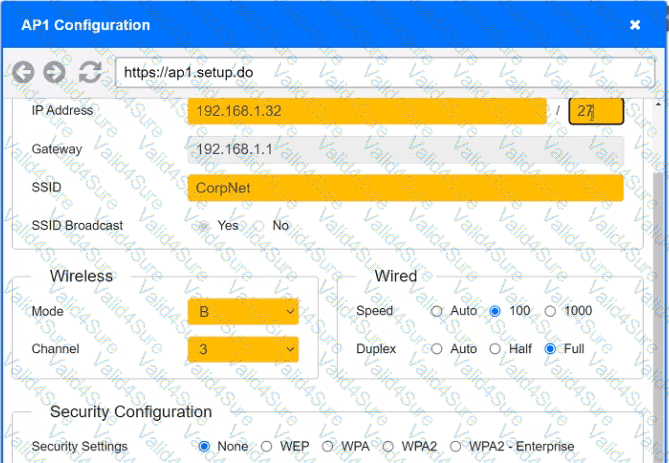
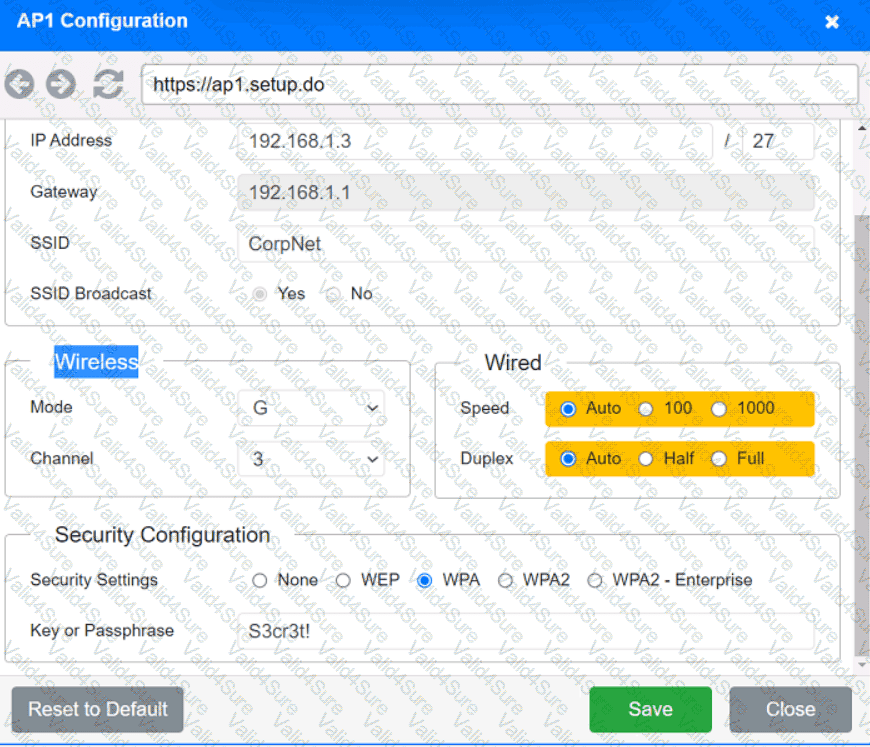
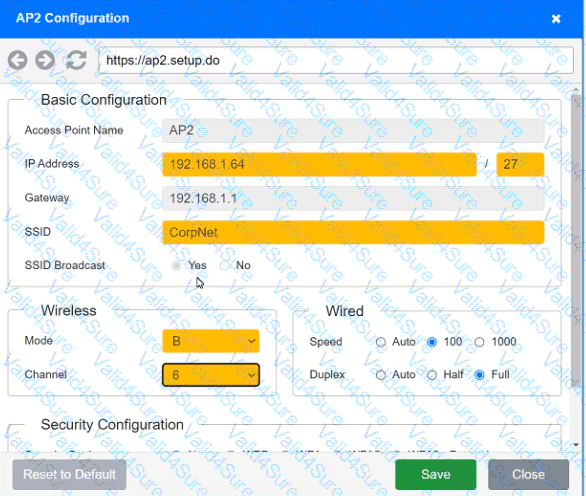
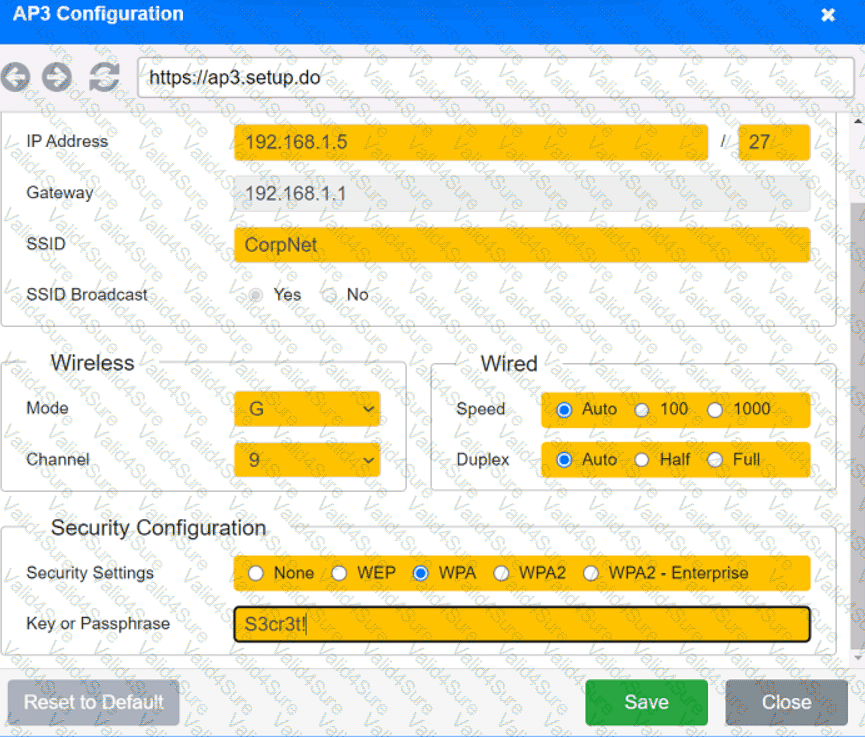
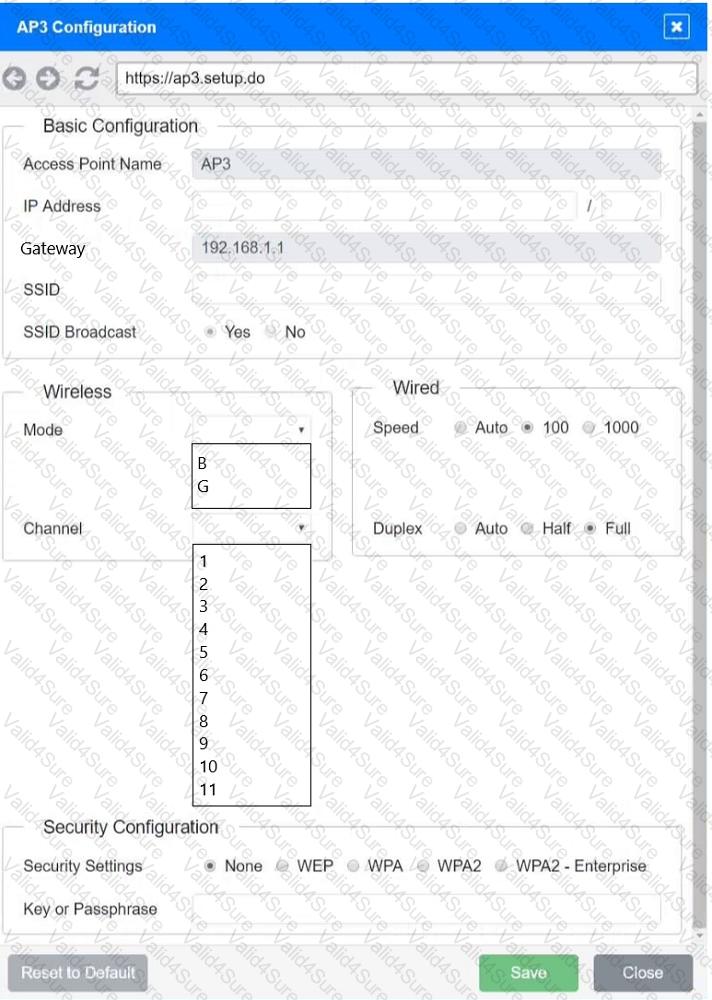
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other
The subnet the Access Points and switch are on should only support 30 devices maximum
The Access Points should be configured to only support TKIP clients at a maximum speed
INSTRUCTONS
Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following routing protocols uses an autonomous system number?
A company recently converted most of the officelaptops to connect wirelesslyto the corporate network. After ahigh-traffic malware attack, narrowing the event to a specific user wasdifficultbecause of thewireless configuration.
Which of the following actions should the company take?
A group of users cannot connect to network resources. The technician runs ipconfig from one user's device and is able to ping the gateway shown from the command. Which of the following is most likely preventing the users from accessing network resources?