N10-009 Exam Dumps - CompTIA Network+ Certification Exam
Searching for workable clues to ace the CompTIA N10-009 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s N10-009 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following is most closely associated with having a leased line to a public cloud provider?
Which of the following ports should a network administrator enable for encrypted login to a network switch?
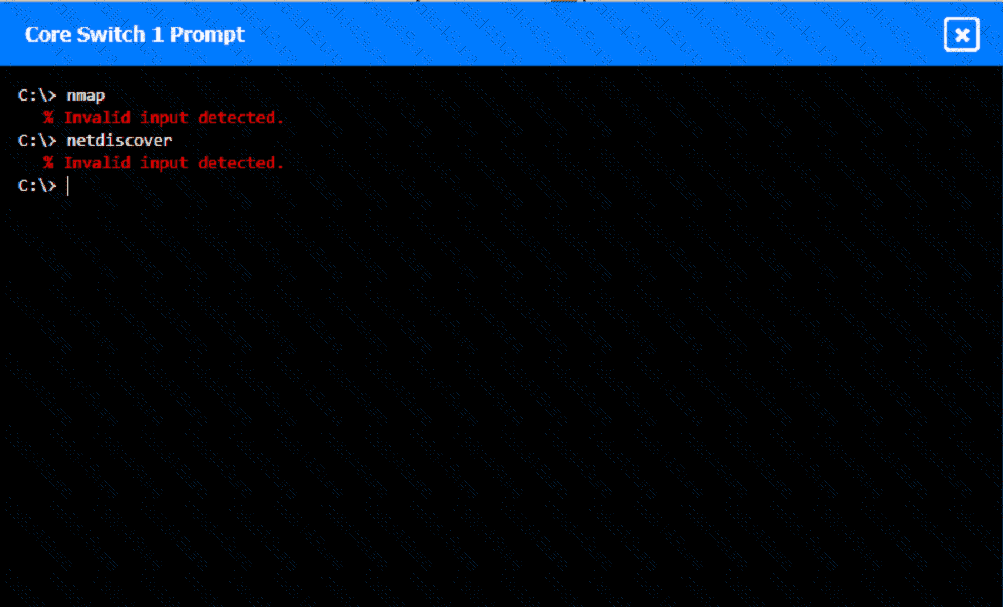
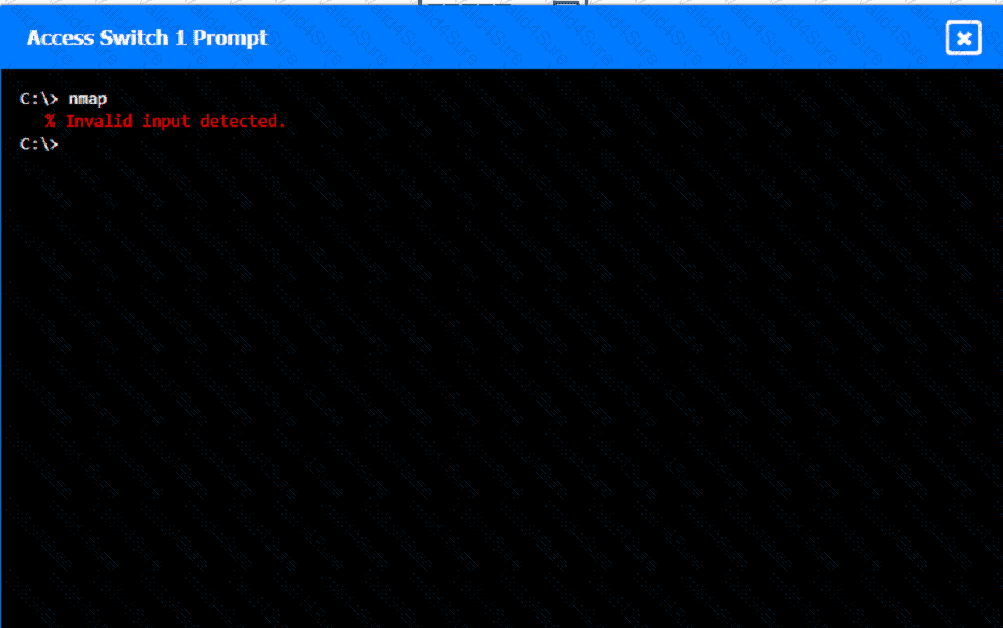
A network technician was recently onboarded to a company. A manager has
tasked the technician with documenting the network and has provided the technician With partial information from previous documentation.
Instructions:
Click on each switch to perform a network discovery by entering commands into the terminal. Fill in the missing information using drop-down menus provided.
In the troubleshooting methodology, which of the following actions comes after verifying that the initial problem has been resolved?
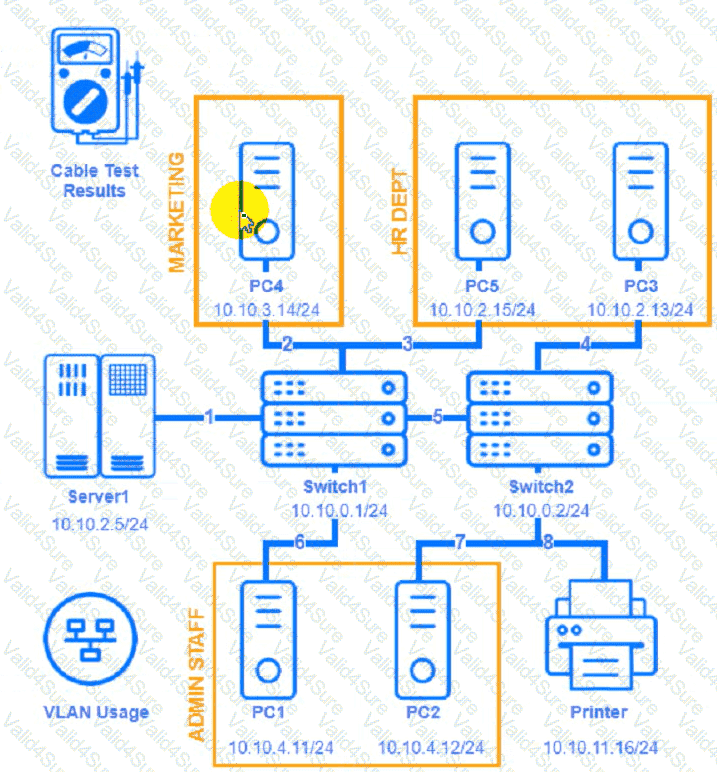
A network technician needs to resolve some issues with a customer ' s SOHO network.
The customer reports that some of the devices are not connecting to the network, while others appear to work as intended.
INSTRUCTIONS
Troubleshoot all the network components and review the cable test results by Clicking on each device and cable.
Diagnose the appropriate component(s) by identifying any components with a problem and recommend a solution to correct each problem.


Cable Test Results:
Cable 1:
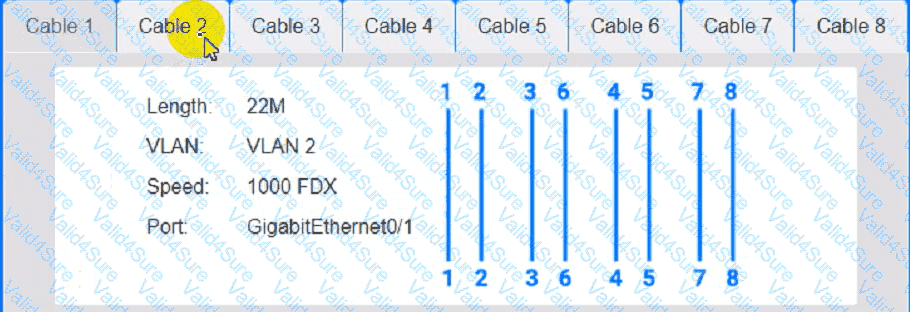
Cable 2:
Cable 3:
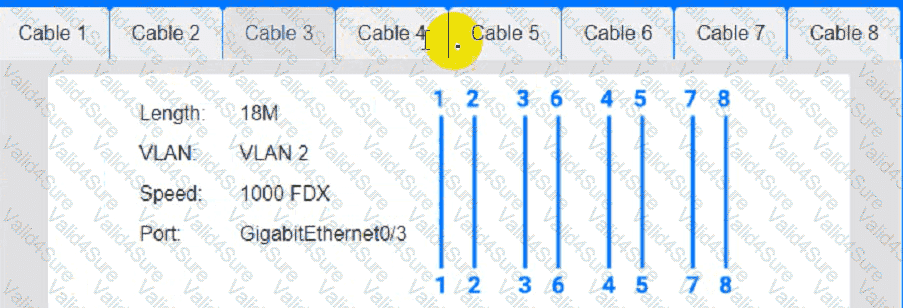
Cable 4:
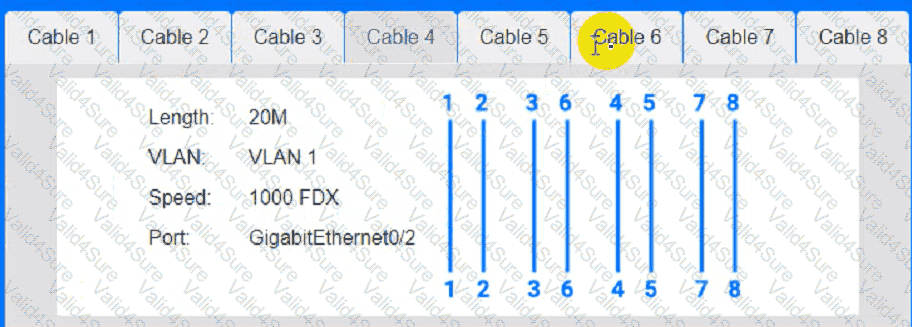
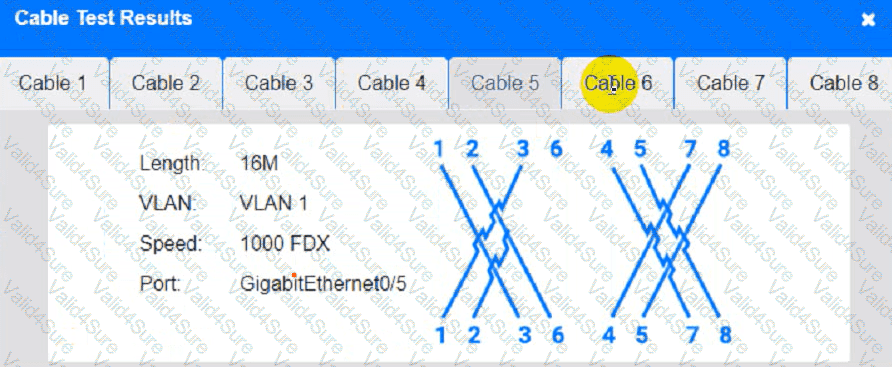
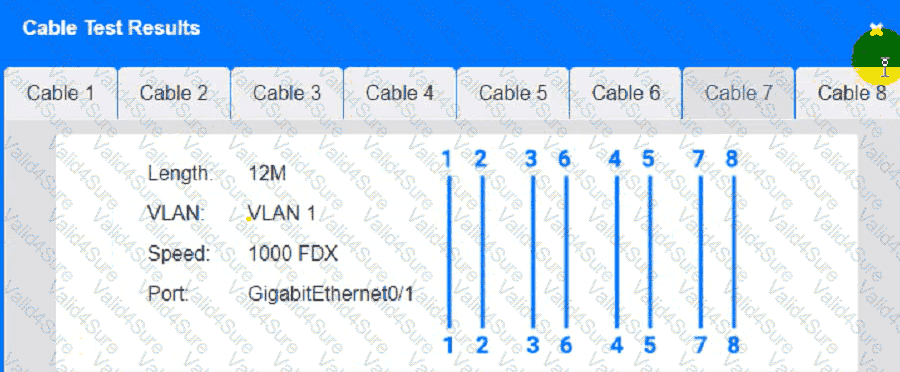
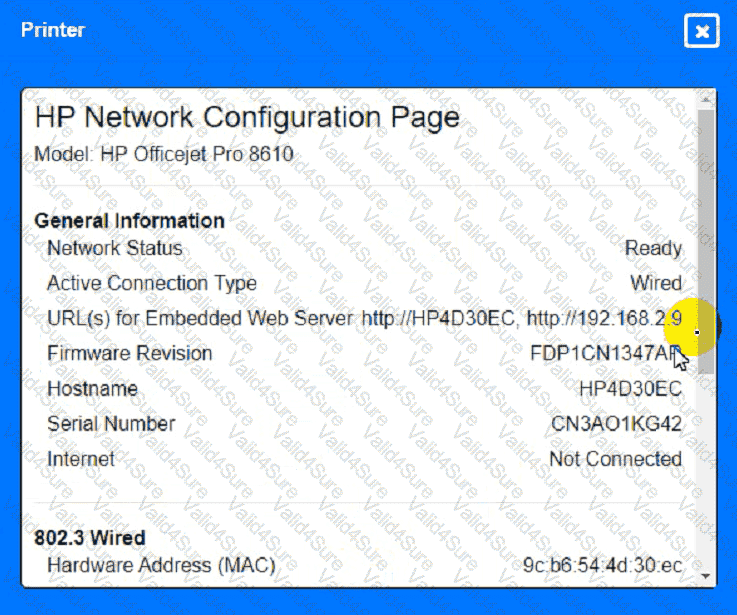
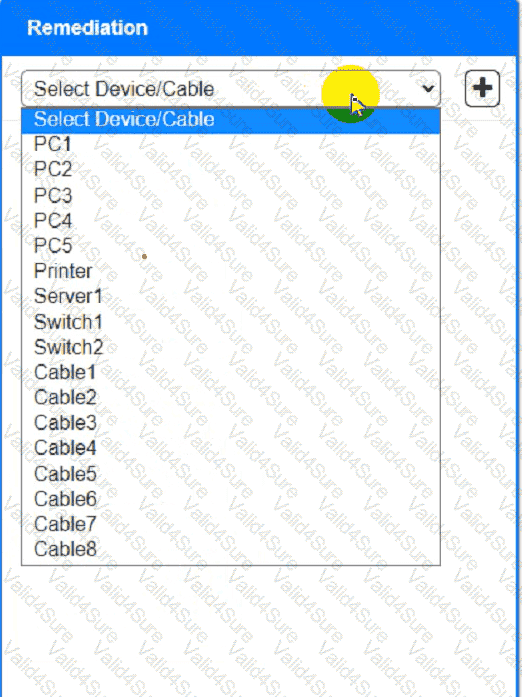
A network administrator is troubleshooting a connectivity issue between two devices on two different subnets. The administrator verifies that both devices can successfully ping other devices on the same subnet. Which of the following is the most likely cause of the connectivity issue?
A network technician is designing a LAN for a new facility. The company is expecting more than 300 devices to connect to the network. Which of the following masks will provide the most efficient subnet?