PCNSE Exam Dumps - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
An engineer is tasked with deploying SSL Forward Proxy decryption for their organization.
What should they review with their leadership before implementation?
Which three firewall multi-factor authentication factors are supported by PAN-OS? (Choose three.)
An administrator plans to install the Windows-Based User-ID Agent.
What type of Active Directory (AD) service account should the administrator use?
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed.
Which set of actions should the engineer take to achieve this goal?
A firewall administrator configures the HIP profiles on the edge firewall where GlobalProtect is enabled, and adds the profiles to security rules. The administrator wants to redistribute the HIP reports to the data center firewalls to apply the same access restrictions using HIP profiles. However, the administrator can only see the HIP match logs on the edge firewall but not on the data center firewall
What are two reasons why the administrator is not seeing HIP match logs on the data center firewall? (Choose two.)
An engineer must configure a new SSL decryption deployment.
Which profile or certificate is required before any traffic that matches an SSL decryption rule is decrypted?
Review the screenshots.
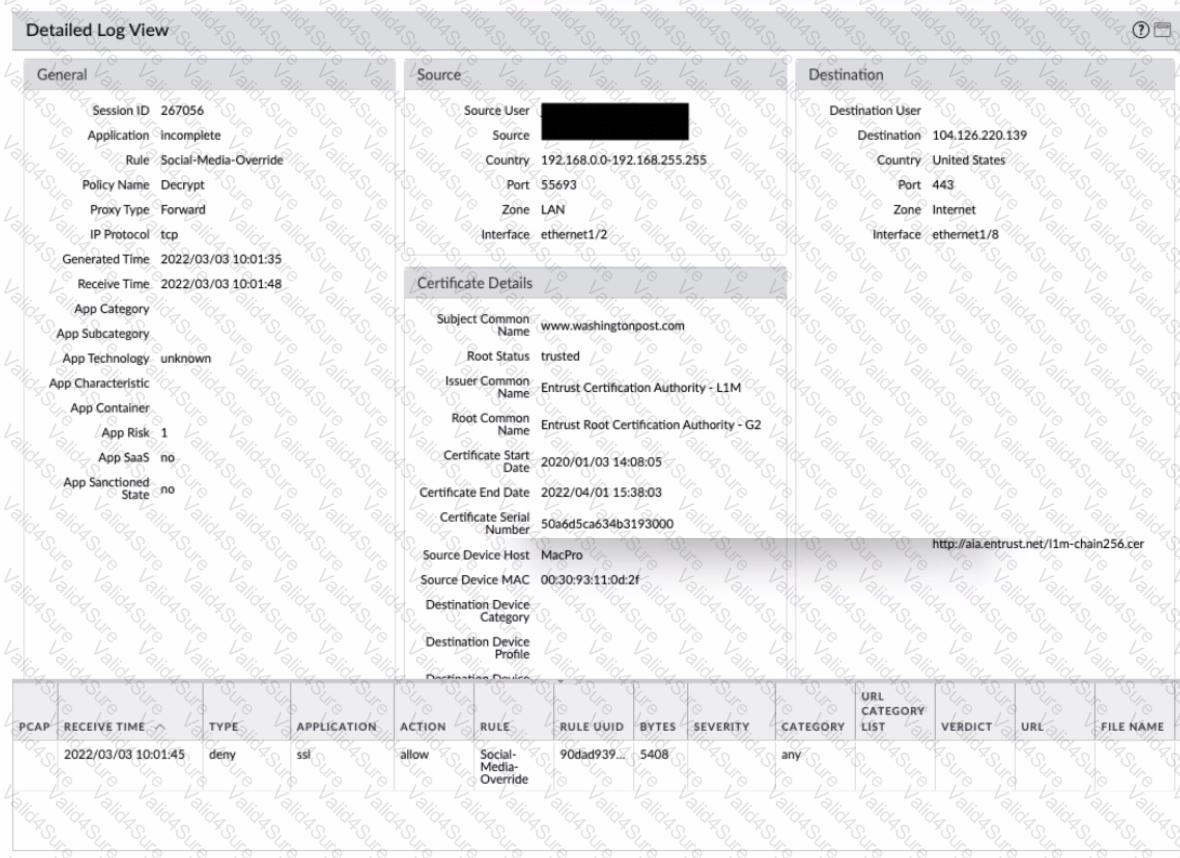
What is the most likely reason for this decryption error log?