H12-821_V1.0 Exam Dumps - HCIP-Datacom-Core Technology V1.0
Searching for workable clues to ace the Huawei H12-821_V1.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-821_V1.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
R1, R2, R3, and R4 run IS-IS, and the DIS priorities of their interfaces are shown in the following figure. Ifall these devices are started simultaneously, will be elected as the DIS. (Enter the device name, for example, R1.)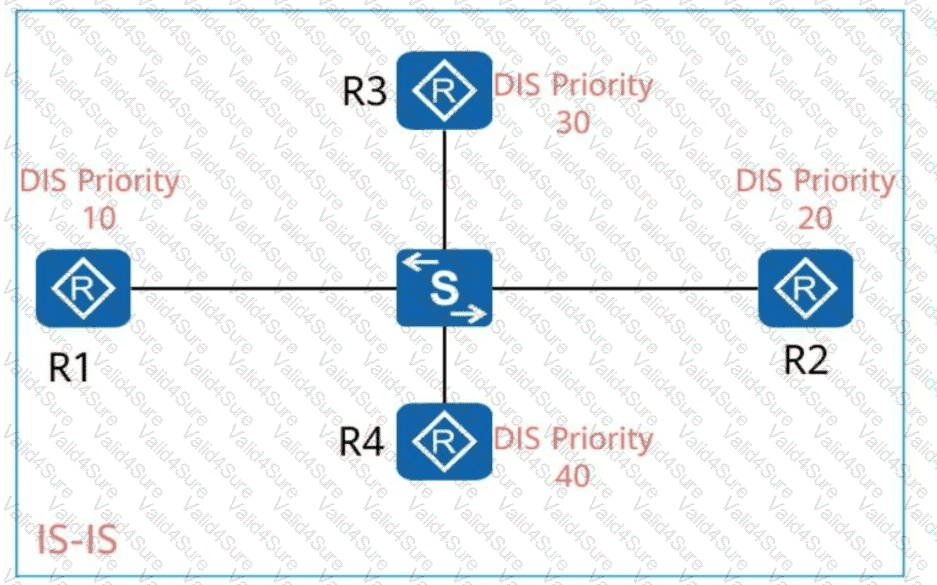
InIPsec, anSA (Security Association)is uniquely identified bythree parameters.Which of the following parameters does not belong to the 3-tuple information?
Huawei modular devices have multiple hardware modules that provide different functions. Match the following hardware modules with their functions.

According to BGP route selection rules, the route with the higher Local_Pref is preferred.
Which of the following is used as the destination port for single-hop BFD?
As shown in the figure, VRRP is associated with a BFD session. When a backup device detects a fault through BFD, the backup device immediately assumes the master role after the Master_Down_Timer timer expires.
A monitoring plane usually comprises the monitoring units of main control boards and interface boards. This plane can monitor the system environment independently. Which of the following environment monitoring functions can be provided by the monitoring plane?