PSP Exam Dumps - Planning & Scheduling Professional (PSP) Exam
Searching for workable clues to ace the AACE International PSP Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PSP PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
If drafting of the product manual overruns its planned duration by 5 days, how many days may the manufacturing be delayed without affecting release of the product?
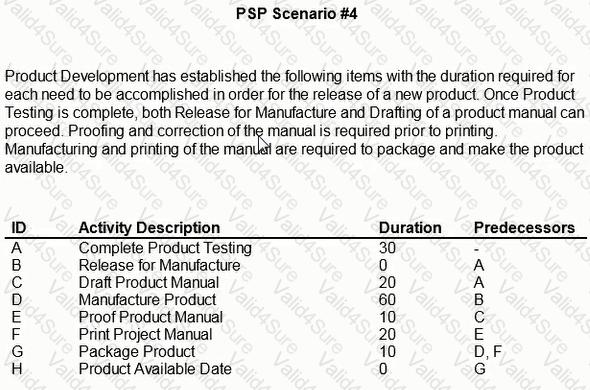
How many workdays occur from the start of the Product Testing to the Product Available milestone?
Which of the following risks CANNOT be estimated by BILCO with only a resource-loaded schedule?
